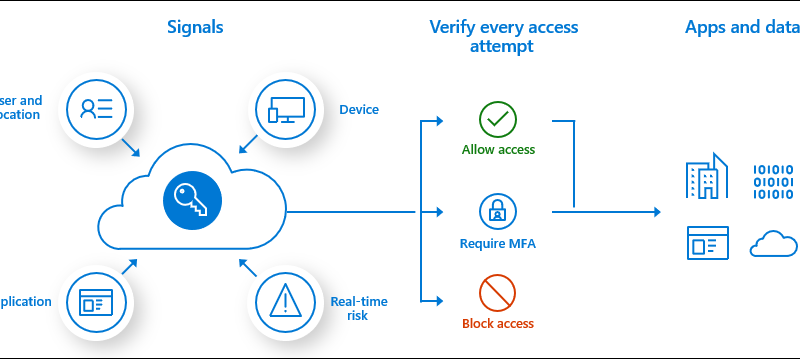
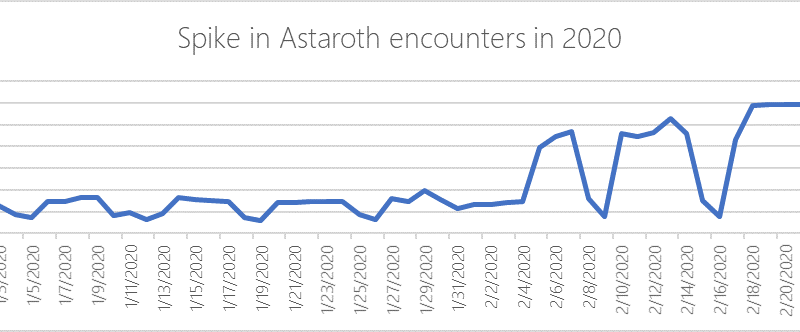
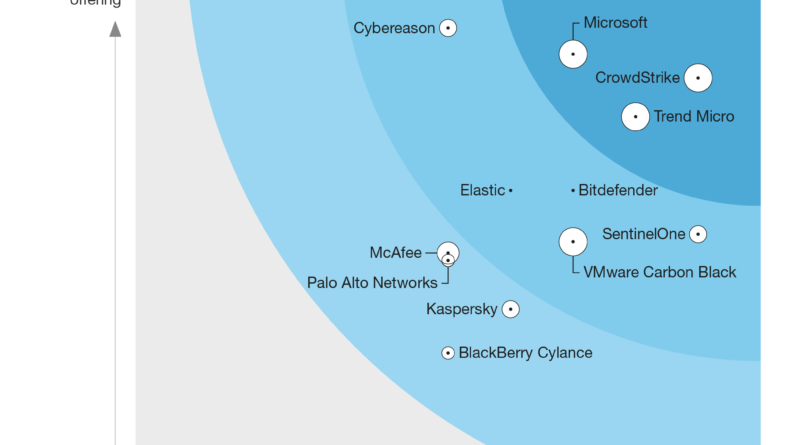
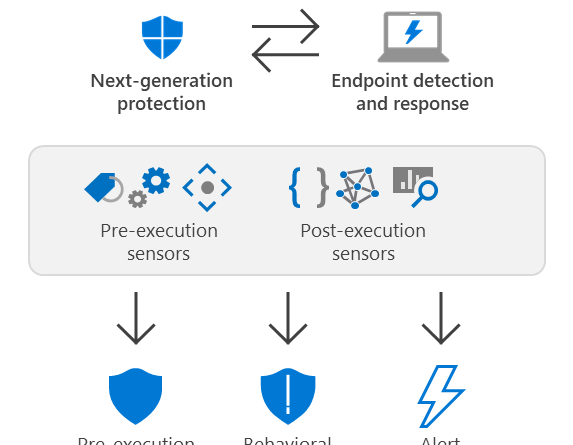
Microsoft works with healthcare organizations to protect from popular ransomware during COVID-19 crisis: Here’s what to do
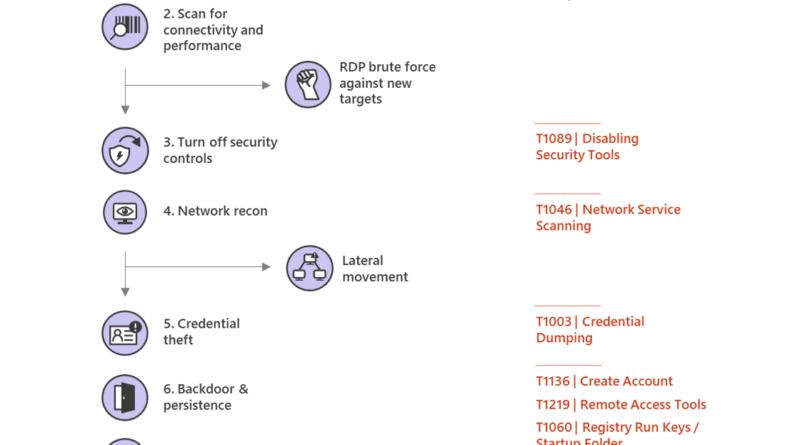
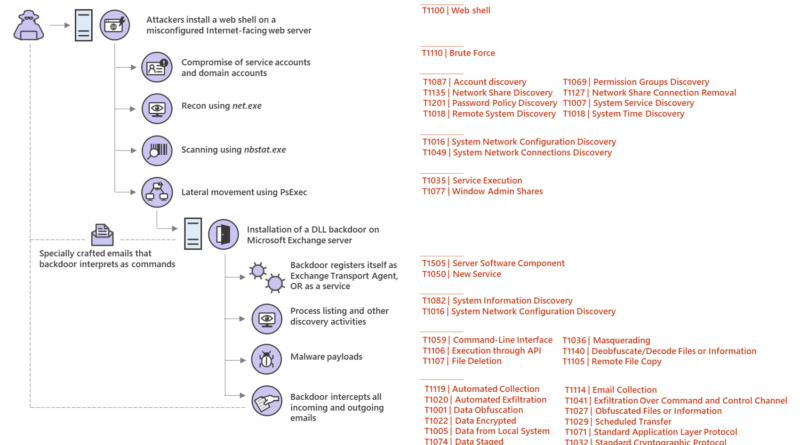
Microsoft identified several dozens of hospitals with vulnerable gateway and VPN appliances. We sent these hospitals a first-of-its-kind notification with important info about the vulnerabilities, how attackers can take advantage of them, and a strong recommendation to apply security updates.
The post Microsoft works with healthcare organizations to protect from popular ransomware during COVID-19 crisis: Here’s what to do appeared first on Microsoft Security. READ MORE HERE…