Stopping Carbanak+FIN7: How Microsoft led in the MITRE Engenuity® ATT&CK® Evaluation
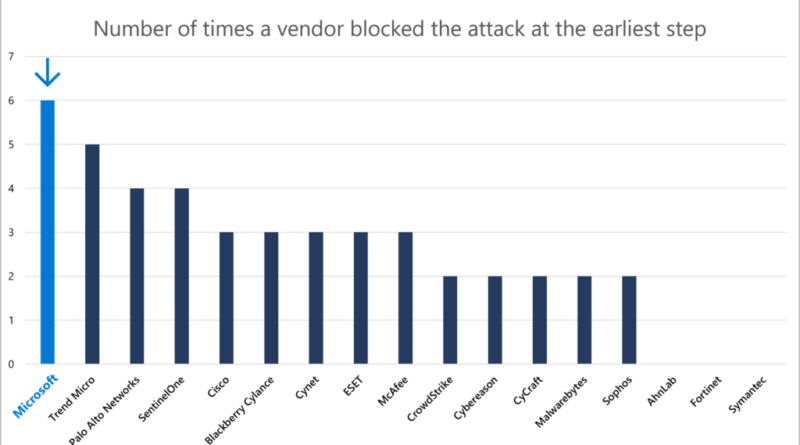
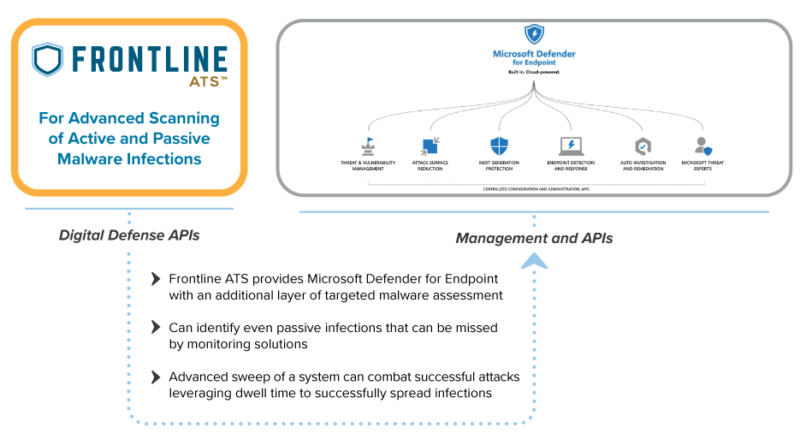
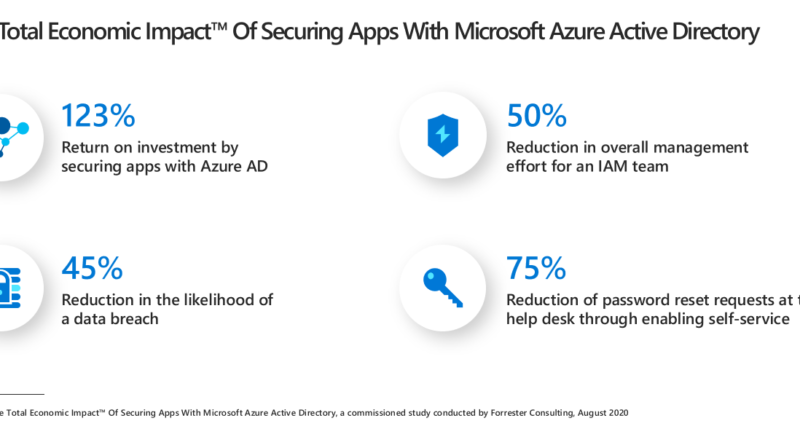
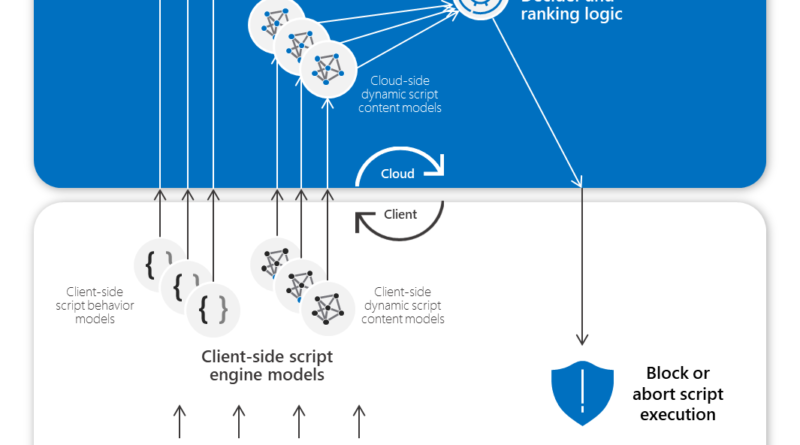
In MITRE Engenuity’s recent Carbanak+FIN7 ATT&CK Evaluation, Microsoft demonstrated that we can stop advanced, real-world attacks by threat actor groups with our industry-leading security capabilities. In this year’s evaluation, we engaged our unified Microsoft 365 Defender stack, with market-leading capabilities in Microsoft Defender for Endpoint and Microsoft Defender for Identity collaborating to provide: Best overall…
The post Stopping Carbanak+FIN7: How Microsoft led in the MITRE Engenuity® ATT&CK® Evaluation appeared first on Microsoft Security. READ MORE HERE…