Uncovering Trickbot’s use of IoT devices in command-and-control infrastructure
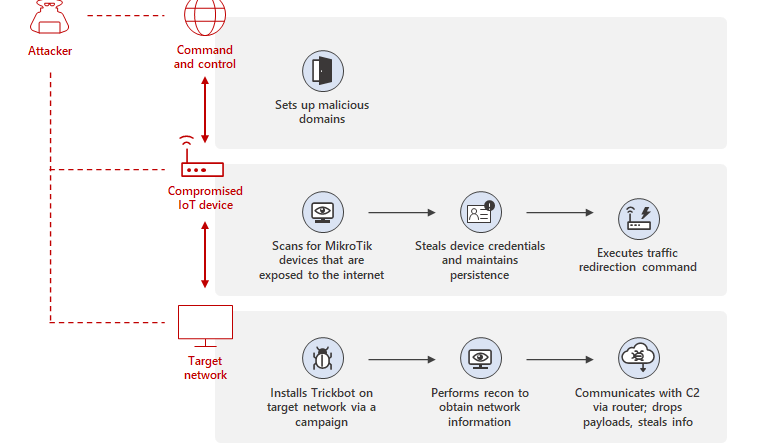
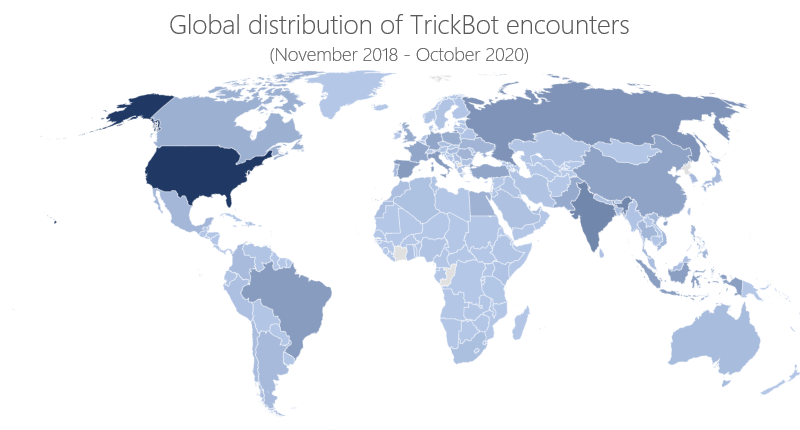
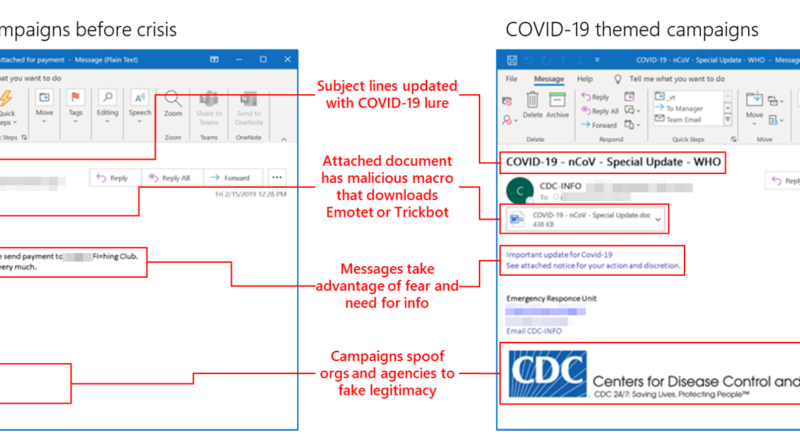
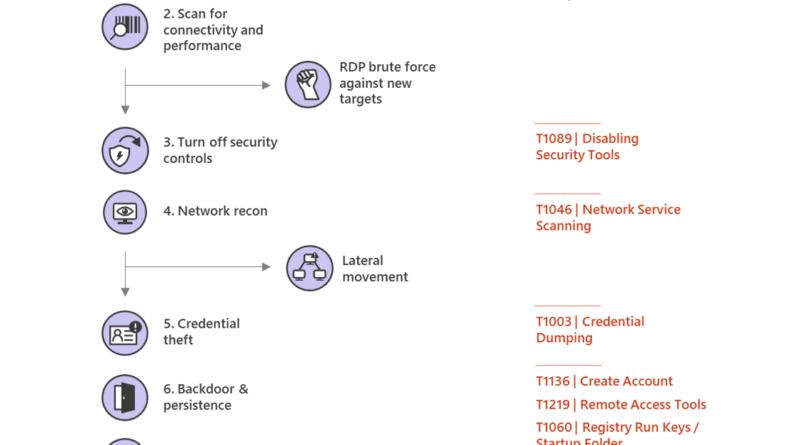
The Microsoft Defender for IoT research team has recently discovered the exact method through which MikroTik devices are used in Trickbot’s C2 infrastructure. In this blog, we share the analysis of this method and provide insights on how attackers gain access and how they use compromised IoT devices in Trickbot attacks.
The post Uncovering Trickbot’s use of IoT devices in command-and-control infrastructure appeared first on Microsoft Security Blog. READ MORE HERE…