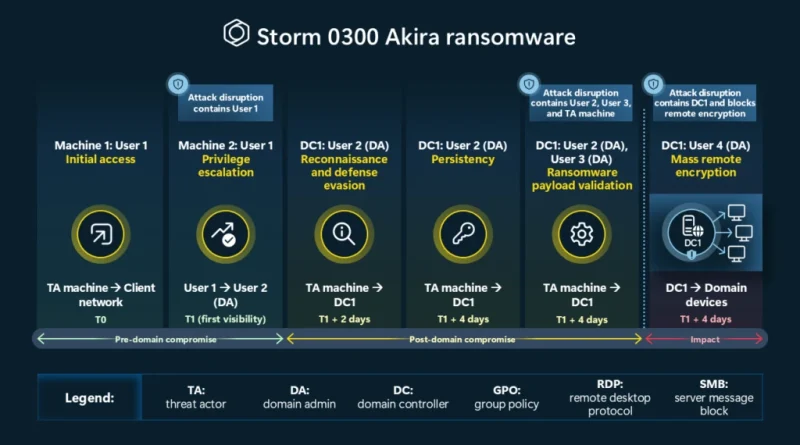
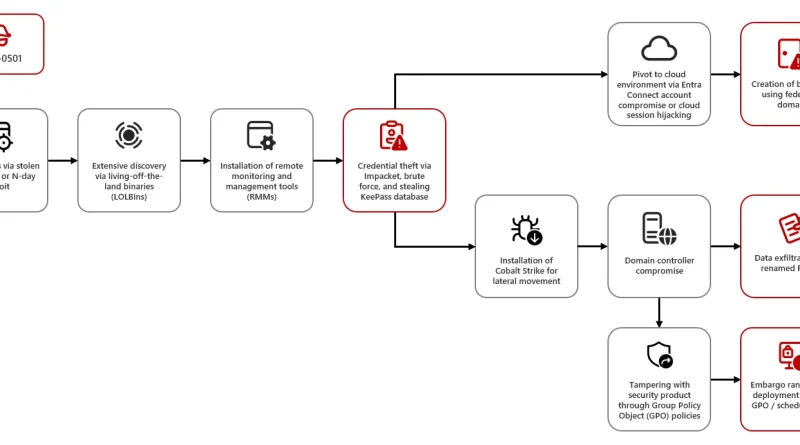
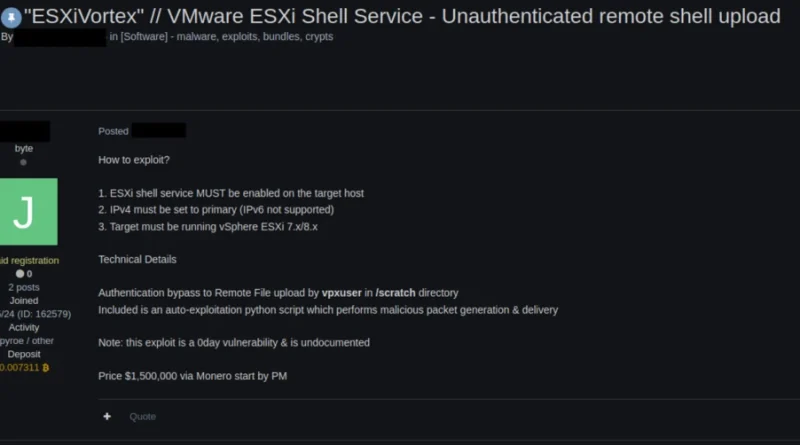
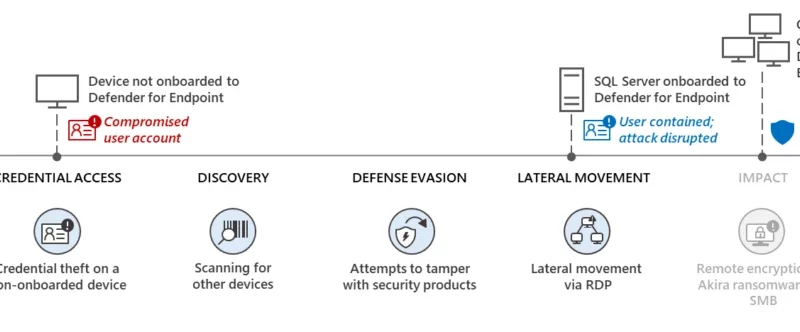
How Microsoft Defender for Endpoint is redefining endpoint security
Learn why many CISOs prefer Microsoft Defender for Endpoint for comprehensive cyberthreat protection across devices and platforms.
The post How Microsoft Defender for Endpoint is redefining endpoint security appeared first on Microsoft Security Blog. READ MORE HERE…