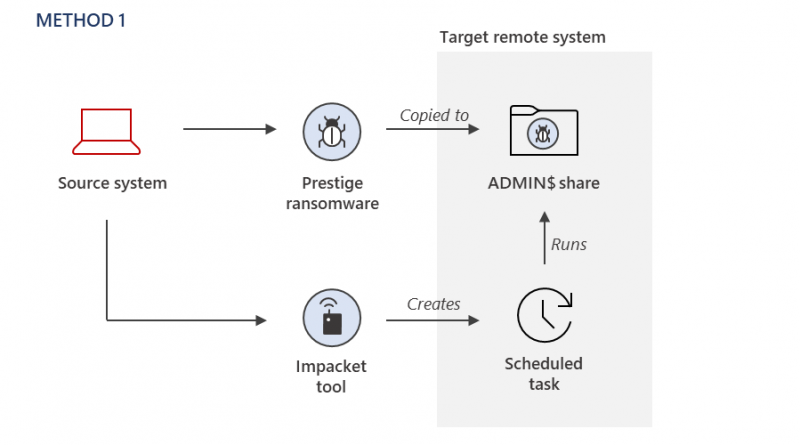
Cloud services and hosting provider Rackspace Technology acknowledged Tuesday that a recent incident that took most of its Hosted Exchange email server business offline was the product of a ransomware attack. The company shut the service down last Friday.It was not, initially, clear what had caused the outage, but Rackspace quickly moved to shift Exchange customers over to Microsoft 365, as this part of the company’s infrastructure was apparently unaffected.Rackpsace offers migration to Microsoft 365
Rackspace said today that there is “no timeline” for a restoration of Exchange service, but it is offering Exchange users technical assistance and free access to Microsoft 365 as a substitute, though it acknowledged that migration is unlikely to be a simple process for every user. Rackspace said that, while the migration is in progress, customers can forward email sent to their Hosted Exchange inboxes to an external server, as a temporary workaround.To read this article in full, please click here READ MORE HERE…
Read More