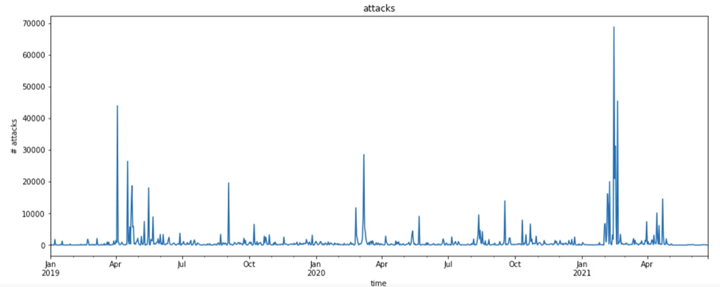
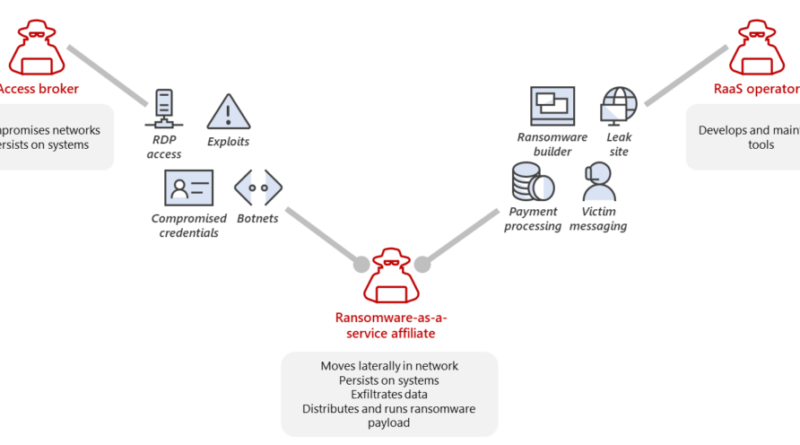
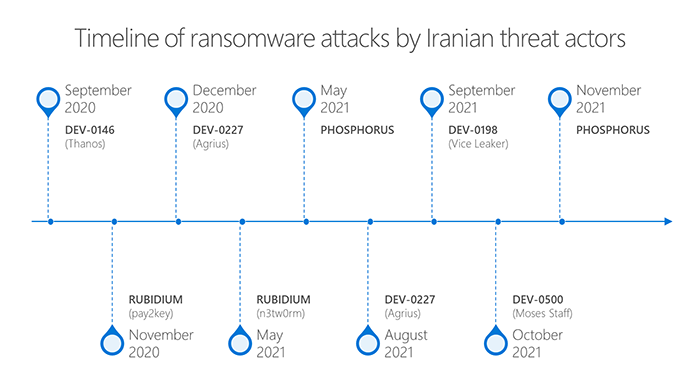
Stop Ransomware with Microsoft Security digital event presents threat intelligence in action
Join the Stop Ransomware with Microsoft Security digital event on September 15, 2022, to learn how to safeguard your organization from today’s attacks—and be ready for tomorrow’s.
The post Stop Ransomware with Microsoft Security digital event presents threat intelligence in action appeared first on Microsoft Security Blog. READ MORE HERE…