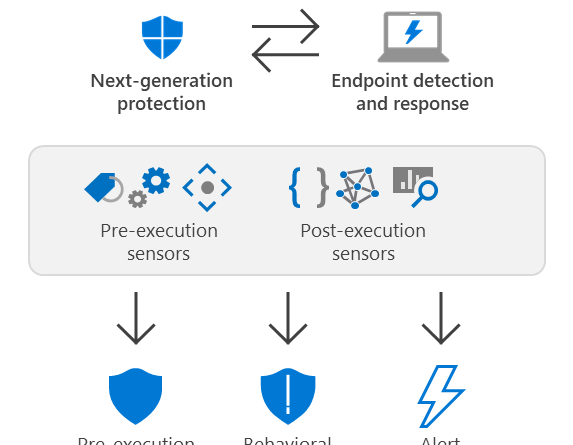
Microsoft Security—detecting empires in the cloud
Microsoft threat analysts have detected another evolution in GADOLINIUM’s tooling that the security community should understand when establishing defenses.
The post Microsoft Security—detecting empires in the cloud appeared first on Microsoft Security. READ MORE HERE…