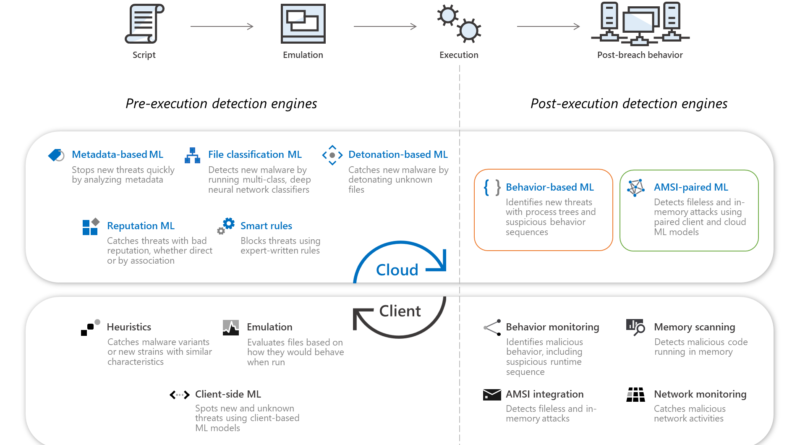
Stopping Active Directory attacks and other post-exploitation behavior with AMSI and machine learning
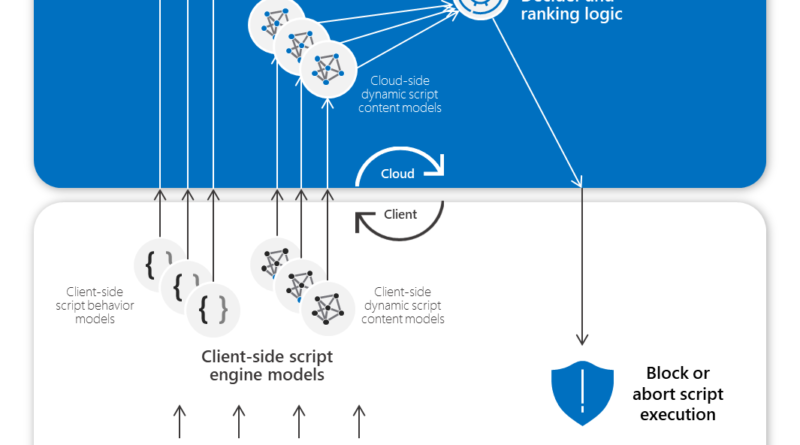
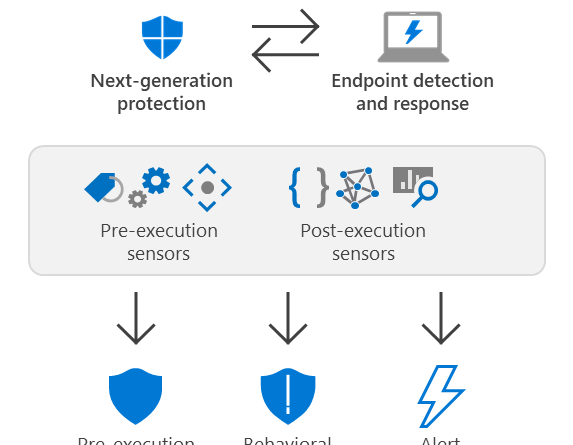
Microsoft Defender ATP leverages AMSI’s visibility into scripts and harnesses the power of machine learning to detect and stop post-exploitation activities that largely rely on scripts.
The post Stopping Active Directory attacks and other post-exploitation behavior with AMSI and machine learning appeared first on Microsoft Security. READ MORE HERE…