Defending Exchange servers under attack
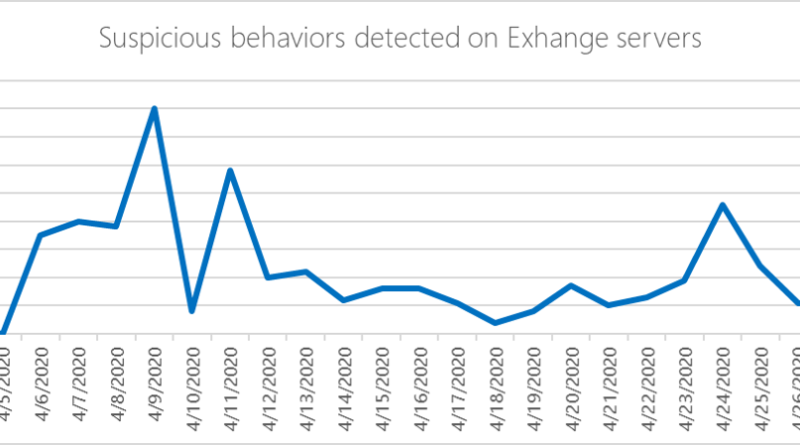
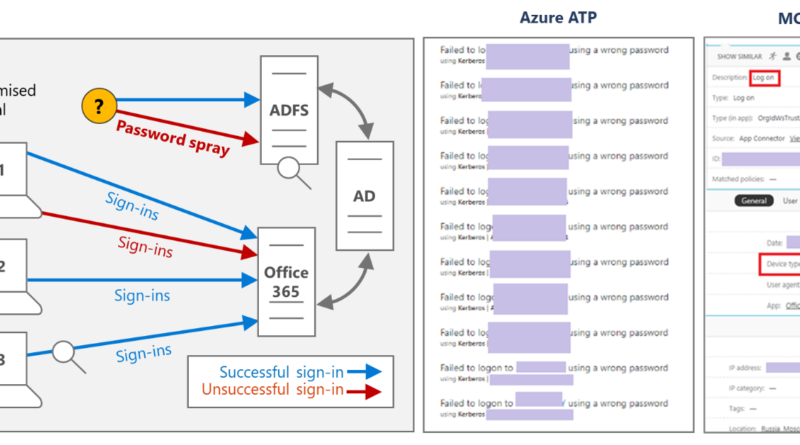
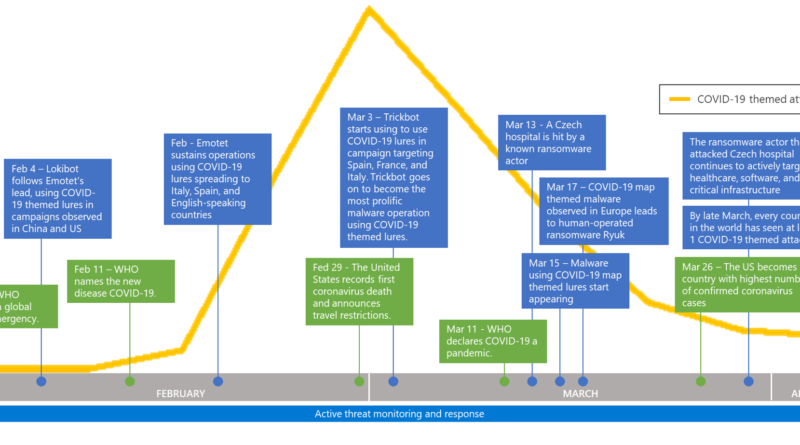
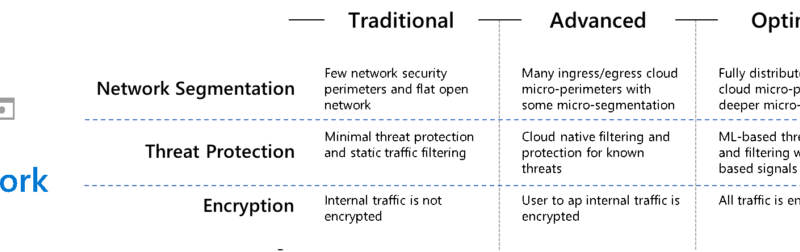
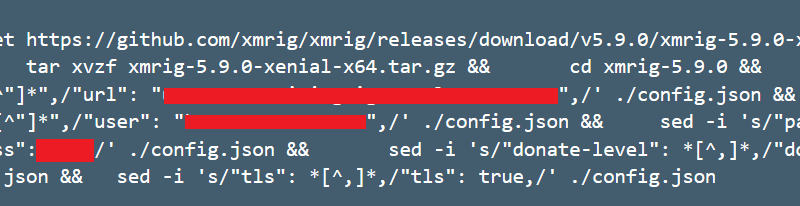
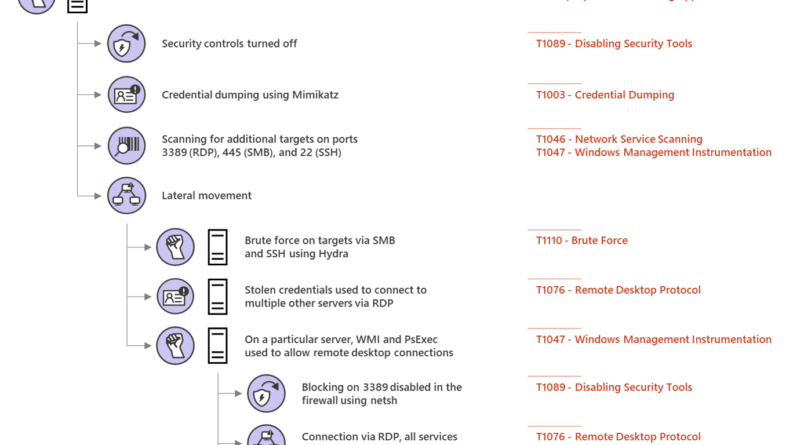
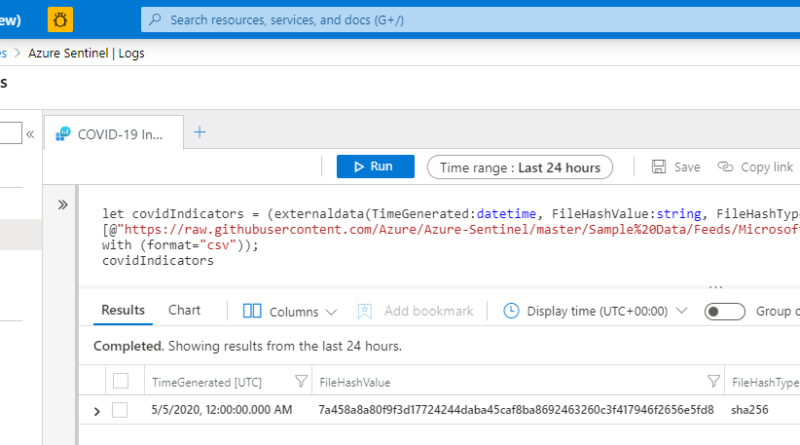
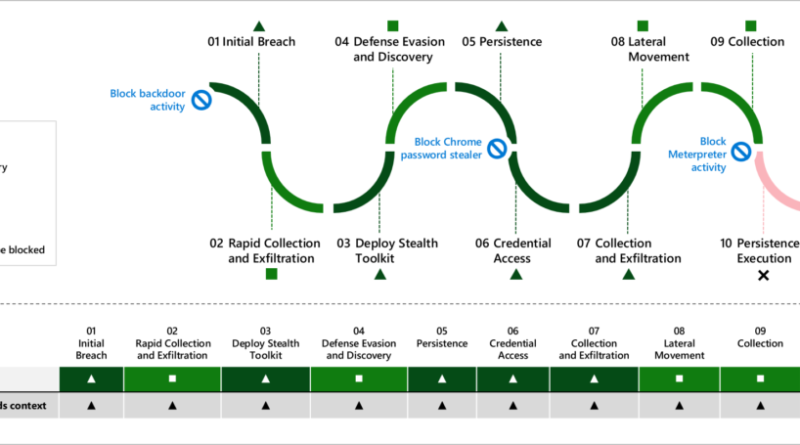
Exchange servers are high-value targets. These attacks also tend to be advanced threats with highly evasive, fileless techniques. Keeping these servers safe from these advanced attacks is of utmost importance.
The post Defending Exchange servers under attack appeared first on Microsoft Security. READ MORE HERE…