Leverage cloud-powered security with Microsoft Defender for IoT
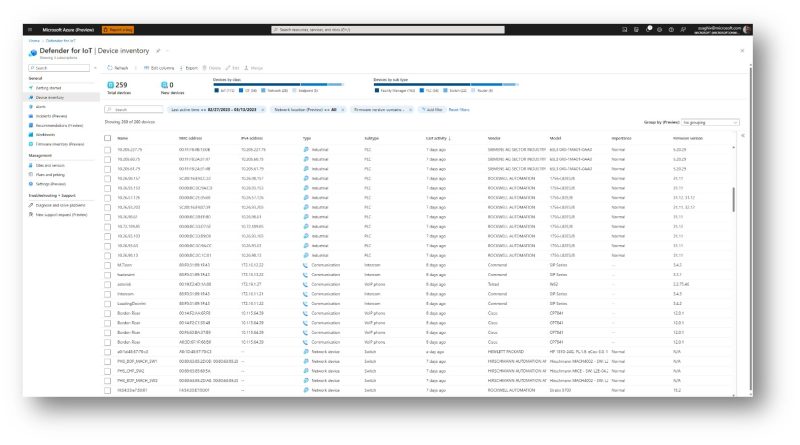
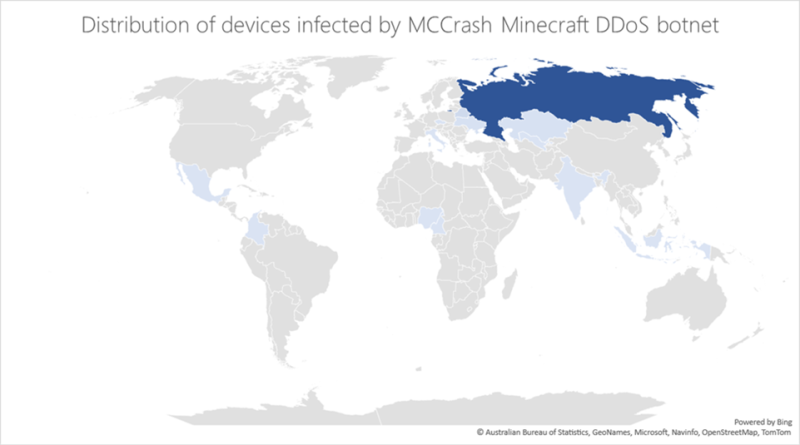
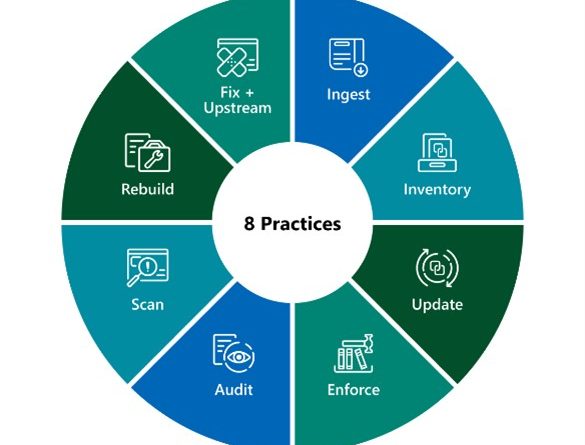
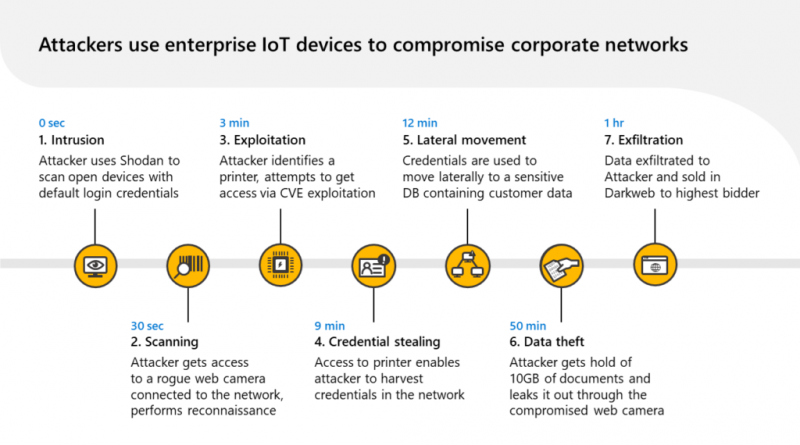
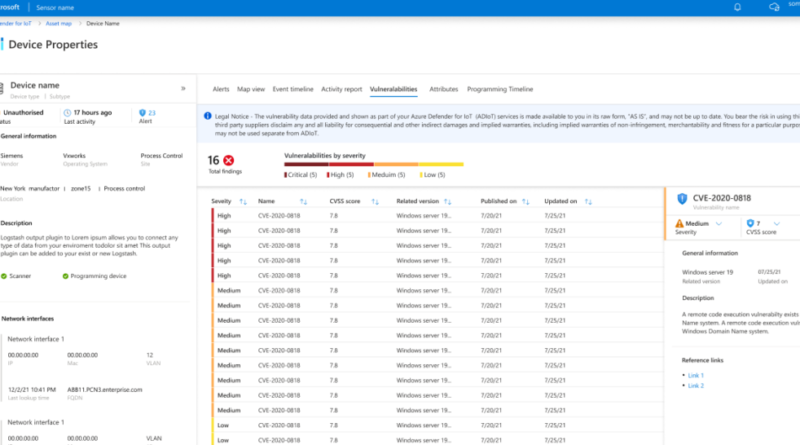
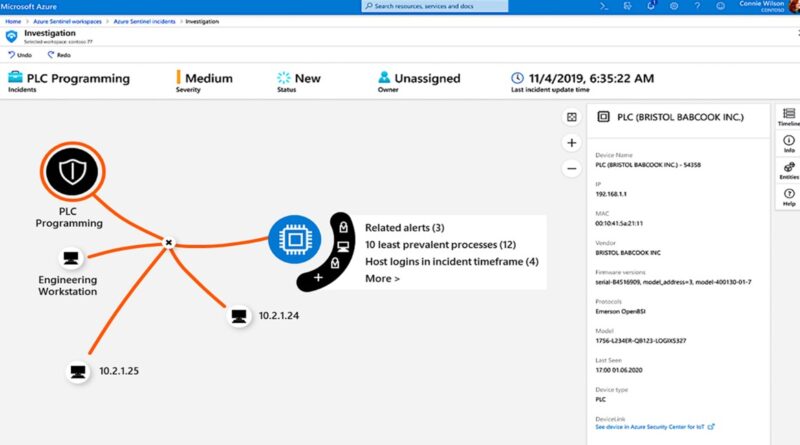
Learn how the new Microsoft Defender for IoT delivers integrated, comprehensive security for your IoT and OT environment. Powered by Microsoft cloud technology, Defender for IoT manages assets, emerging threats, and risks across connected or air-gapped environments—from enterprise networks to mission-critical networks.
The post Leverage cloud-powered security with Microsoft Defender for IoT appeared first on Microsoft Security Blog. READ MORE HERE…