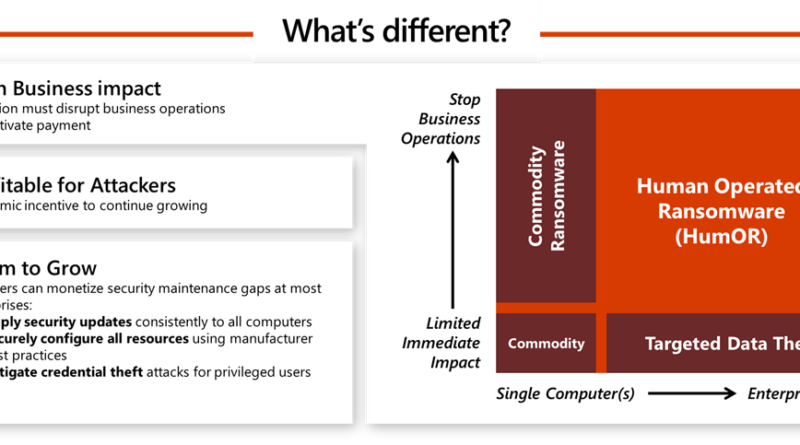
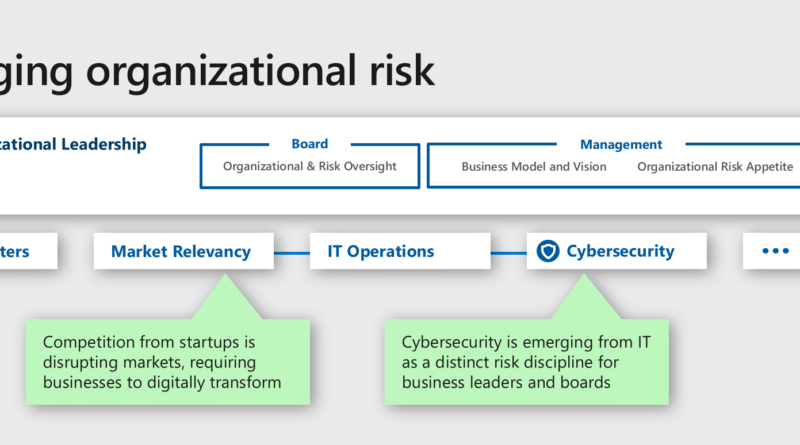
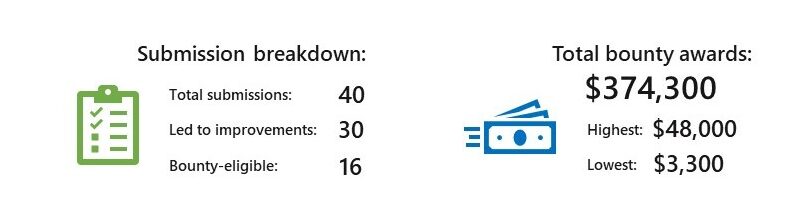
Becoming resilient by understanding cybersecurity risks: Part 3—a security pro’s perspective
Get insights on how to work with business leaders to manage risk and defend against sophisticated cyber threats.
The post Becoming resilient by understanding cybersecurity risks: Part 3—a security pro’s perspective appeared first on Microsoft Security. READ MORE HERE…