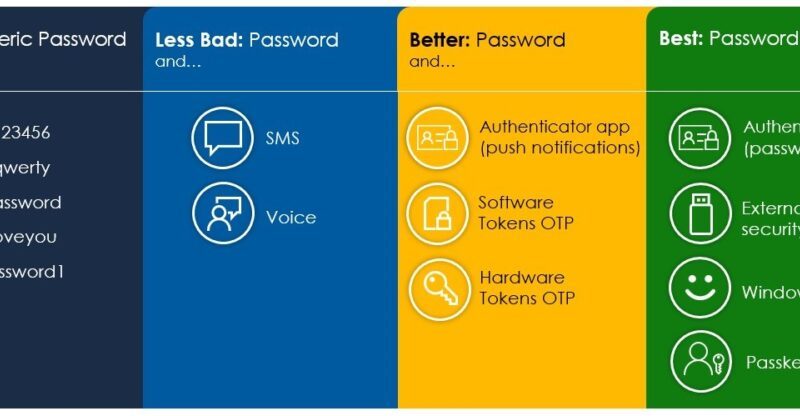
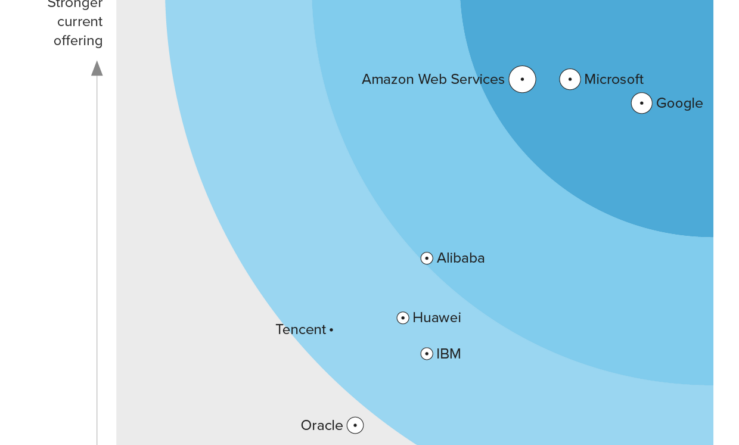
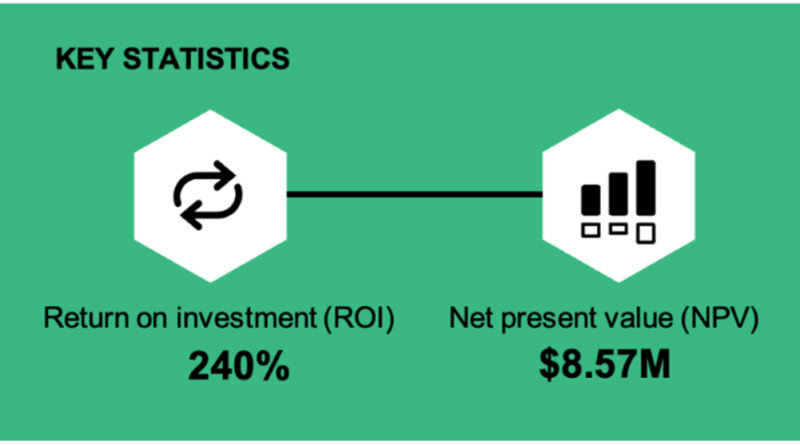
Microsoft Security highlights from RSA Conference 2023
At RSA Conference April 24 to 26, 2023, Microsoft Security shared solution news and insights. Watch Vasu Jakkal’s keynote on-demand (video courtesy of RSA conference).
The post Microsoft Security highlights from RSA Conference 2023 appeared first on Microsoft Security Blog. READ MORE HERE…