Microsoft shifts to a new threat actor naming taxonomy
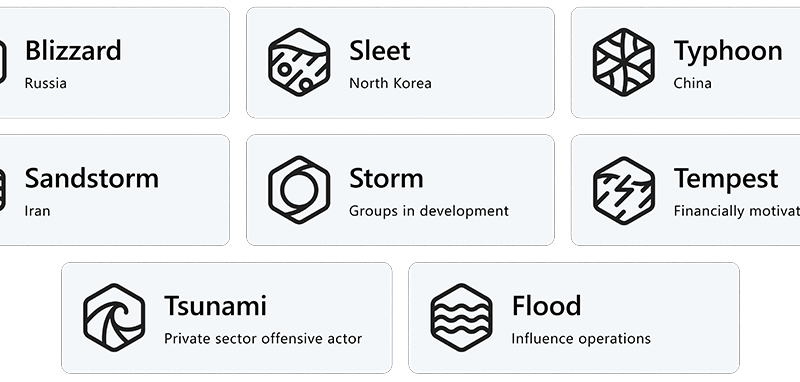
Microsoft is excited to announce that we are shifting to a new threat actor naming taxonomy aligned to the theme of weather. The complexity, scale, and volume of threats is increasing, driving the need to reimagine not only how Microsoft talks about threats but also how we enable customers to understand those threats quickly and with clarity.
The post Microsoft shifts to a new threat actor naming taxonomy appeared first on Microsoft Security Blog. READ MORE HERE…