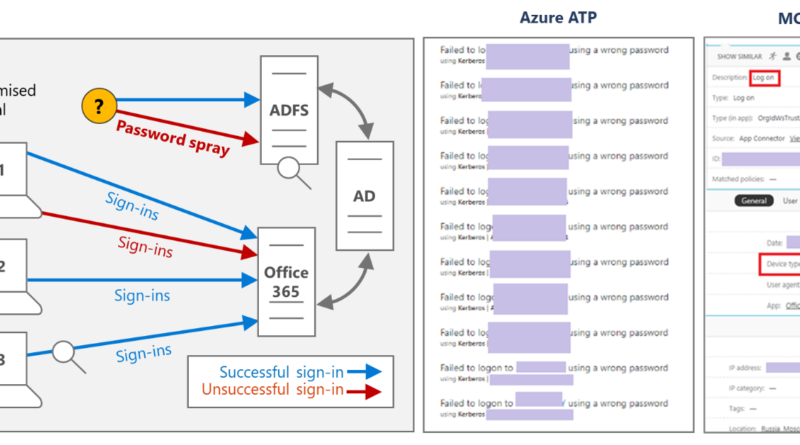
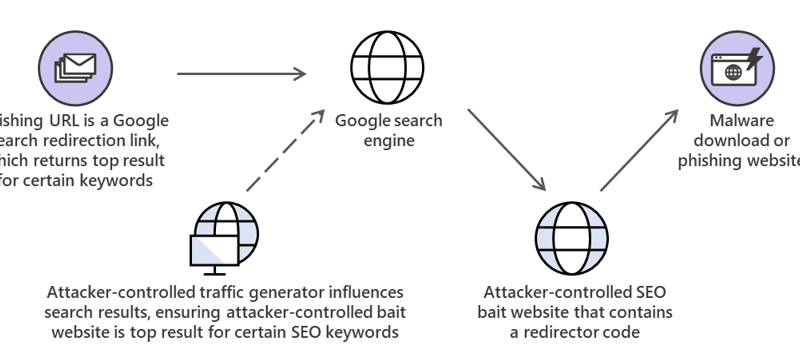
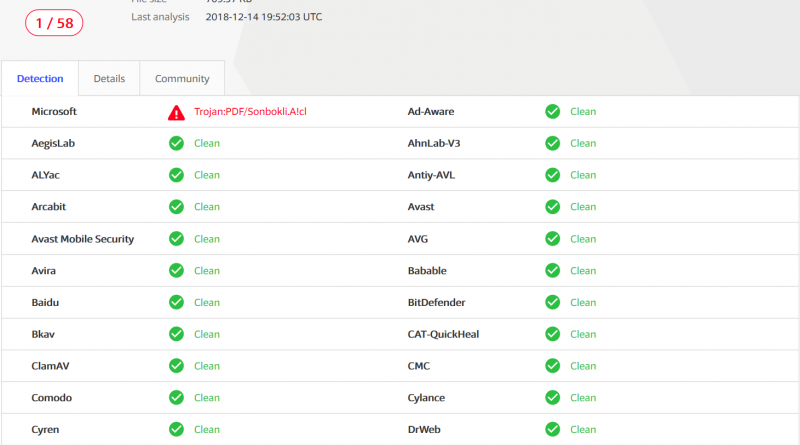
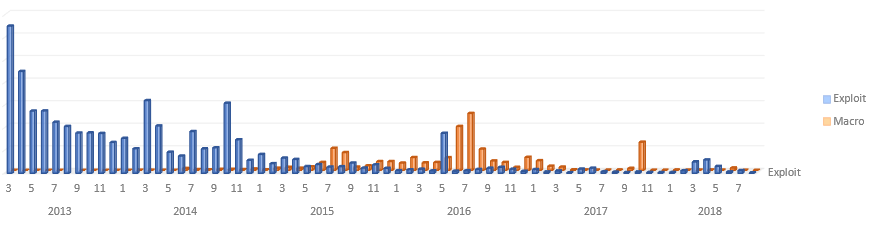
Inside Microsoft Threat Protection: Mapping attack chains from cloud to endpoint
In the first blog in the Inside Microsoft Threat Protection series, we will show how MTP provides unparalleled end-to-end visibility into the activities of nation-state level attacks like HOLMIUM.
The post Inside Microsoft Threat Protection: Mapping attack chains from cloud to endpoint appeared first on Microsoft Security. READ MORE HERE…