CISO Spotlight: How diversity of data (and people) defeats today’s cyber threats
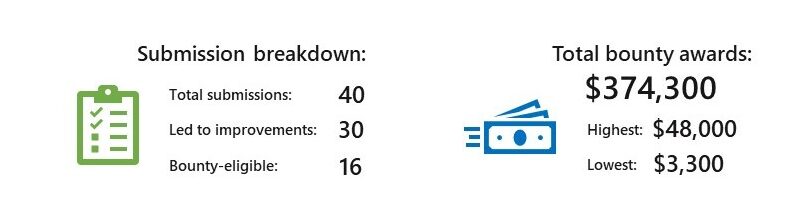
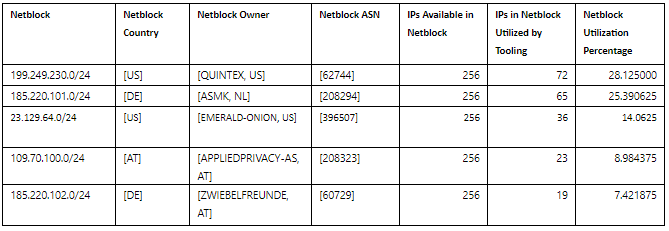
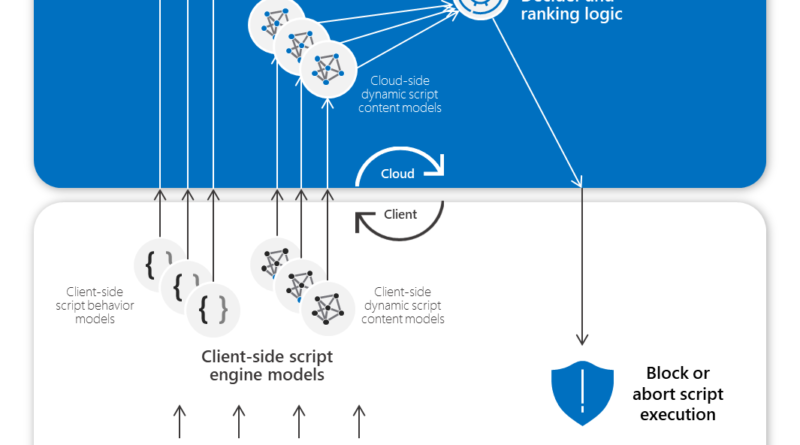
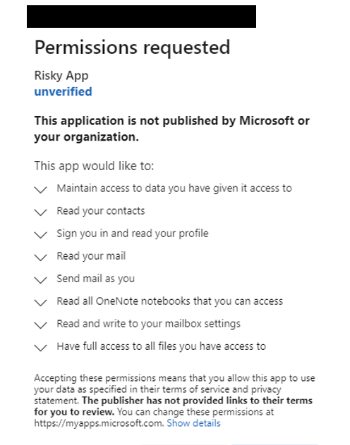
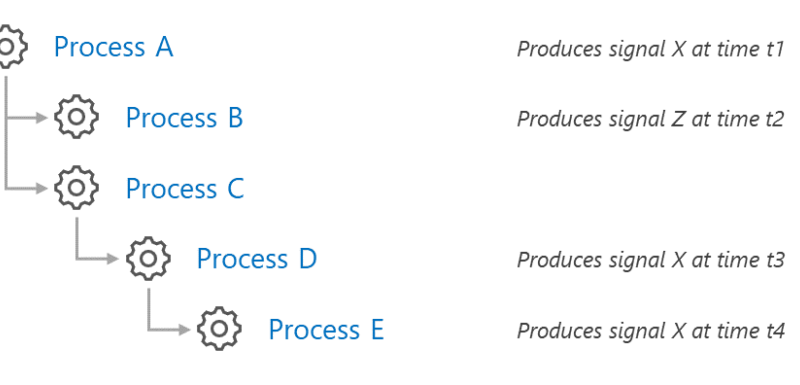
This year, we have seen five significant security paradigm shifts in our industry. This includes the acknowledgment that the greater the diversity of our data sets, the better the AI and machine learning outcomes. This diversity gives us an advantage over our cyber adversaries and improves our threat intelligence. It allows us to respond swiftly…
The post CISO Spotlight: How diversity of data (and people) defeats today’s cyber threats appeared first on Microsoft Security. READ MORE HERE…