IIS modules: The evolution of web shells and how to detect them
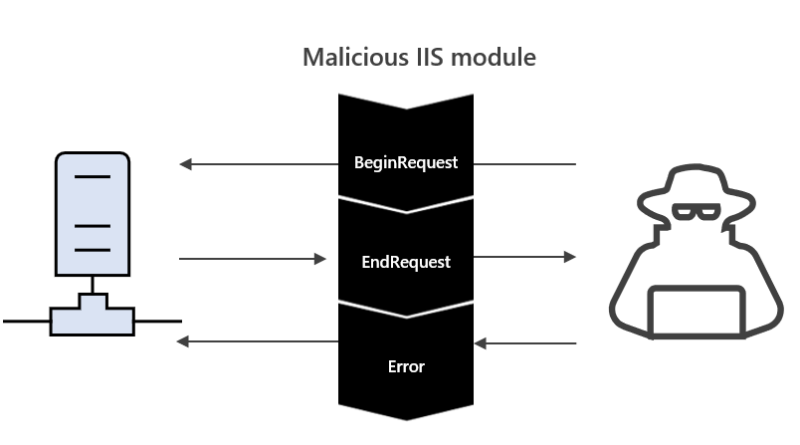
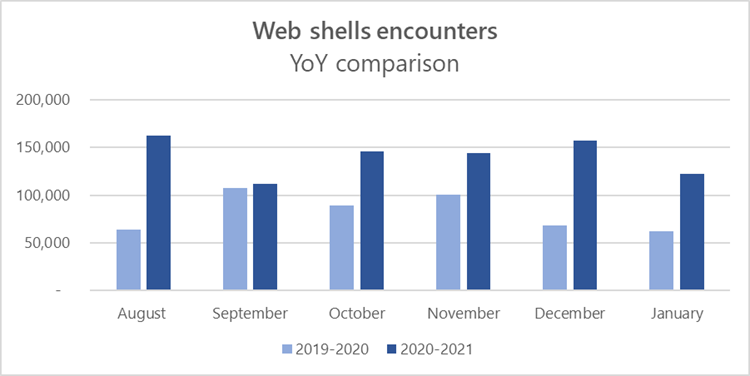
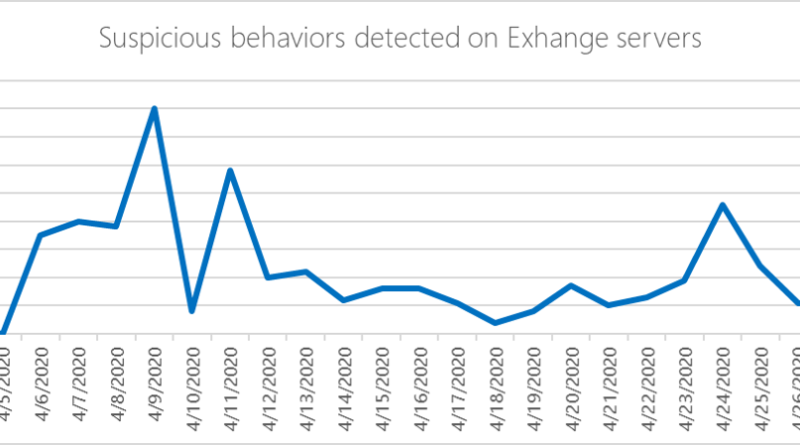
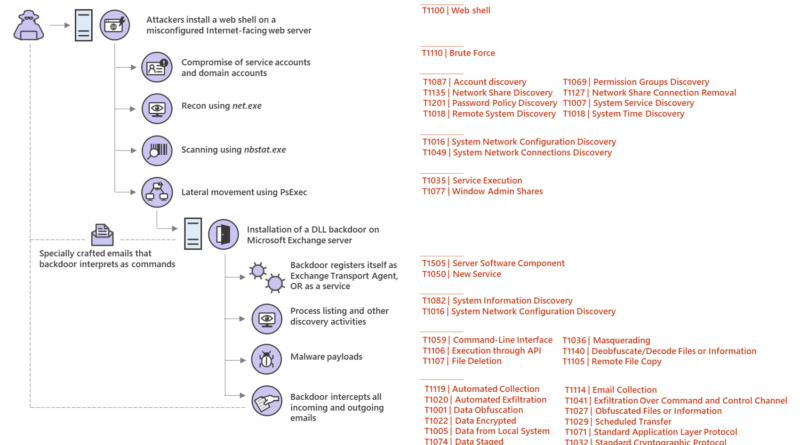
This blog aims to provide further guidance on detecting malicious IIS modules and other capabilities that you can use during your own incident response investigations.
The post IIS modules: The evolution of web shells and how to detect them appeared first on Microsoft Security Blog. READ MORE HERE…