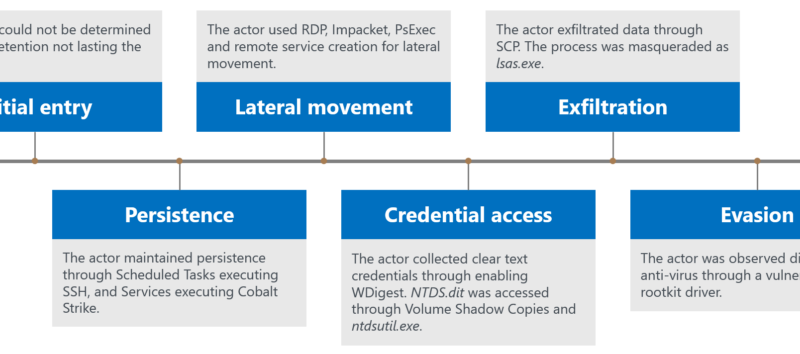
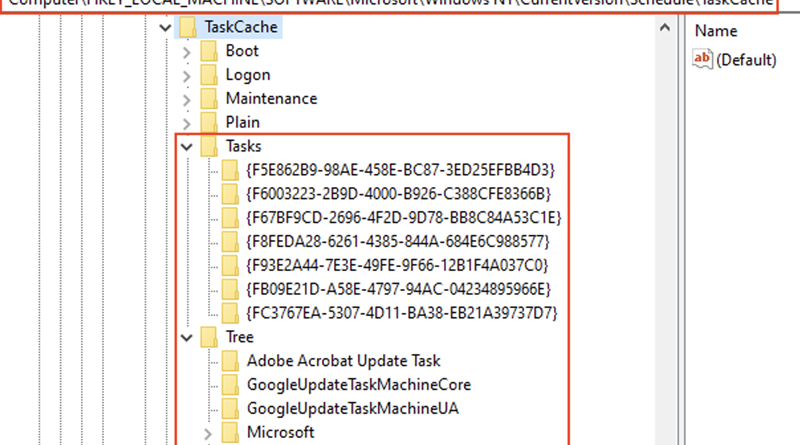
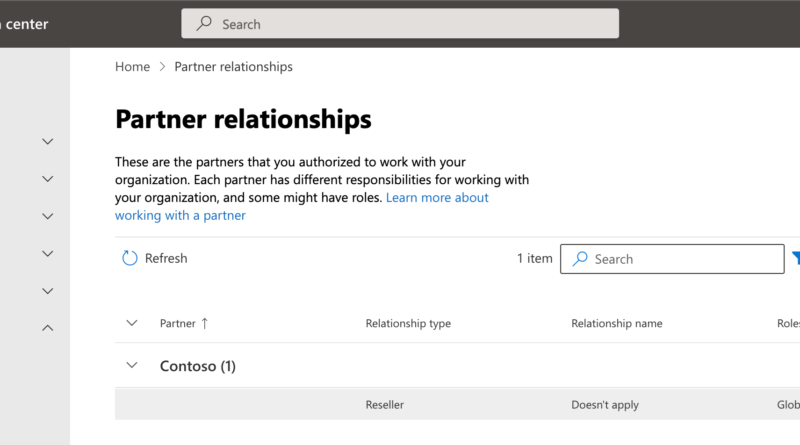
Guidance for investigating attacks using CVE-2022-21894: The BlackLotus campaign
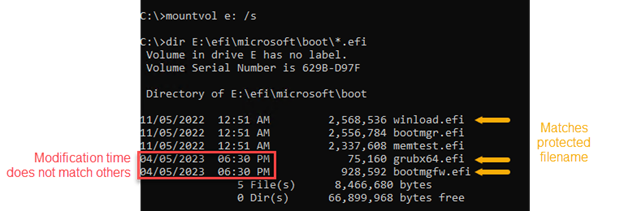
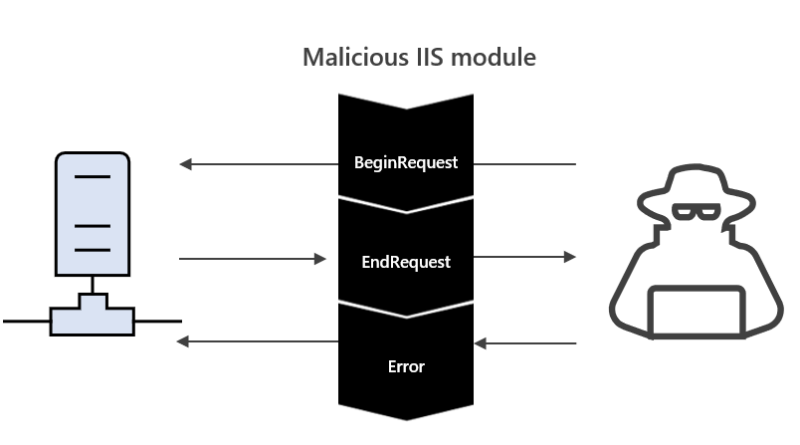
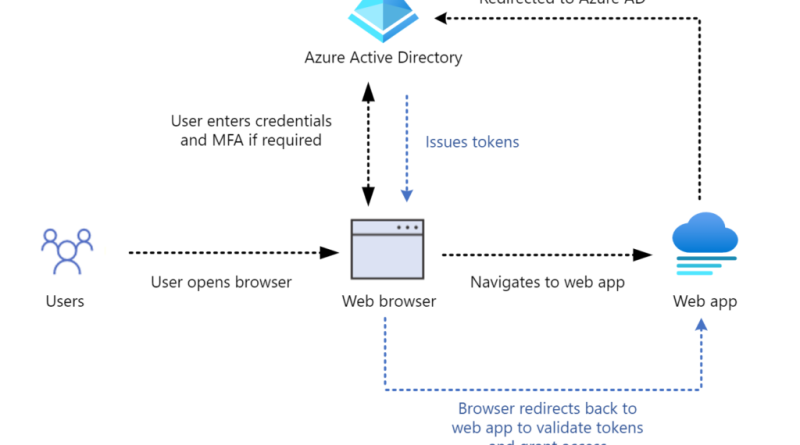
This guide provides steps that organizations can take to assess whether users have been targeted or compromised by threat actors exploiting CVE-2022-21894 via a Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus.
The post Guidance for investigating attacks using CVE-2022-21894: The BlackLotus campaign appeared first on Microsoft Security Blog. READ MORE HERE…