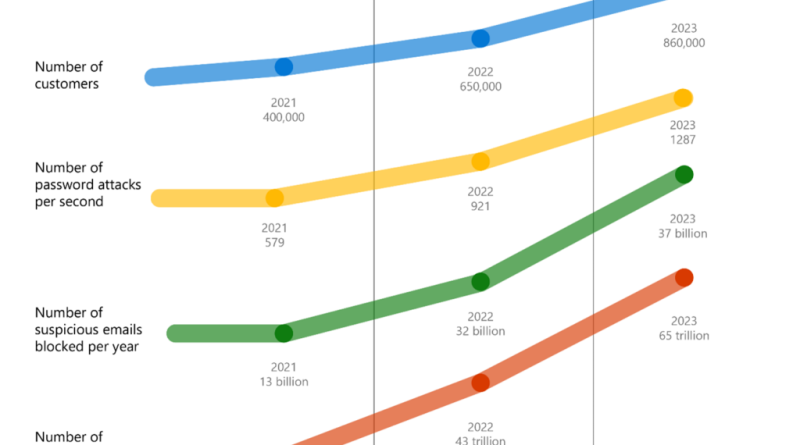
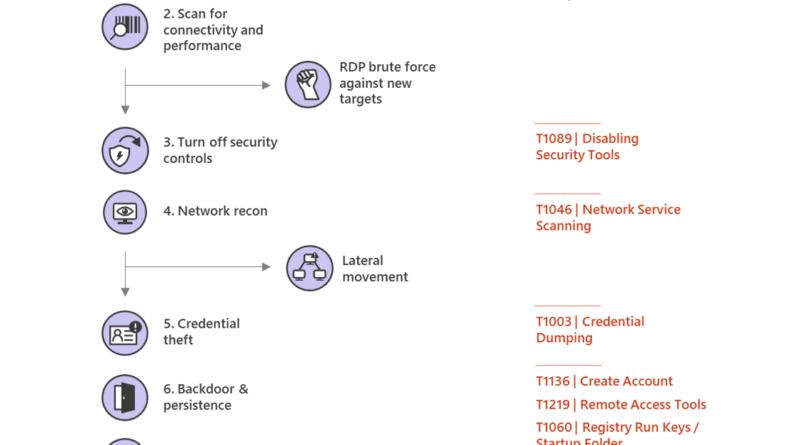
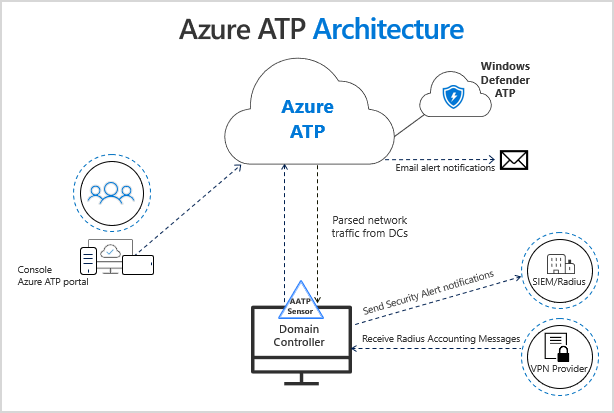
Microsoft Security reaches another milestone—Comprehensive, customer-centric solutions drive results
Learn how Microsoft Security is simplifying security for the new hybrid, multi-platform environment while fostering a diverse new generation of defenders—and how your organization can benefit.
The post Microsoft Security reaches another milestone—Comprehensive, customer-centric solutions drive results appeared first on Microsoft Security Blog. READ MORE HERE…