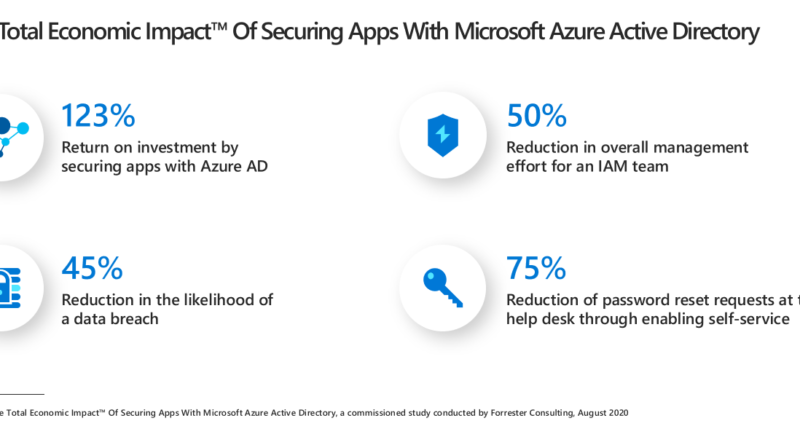
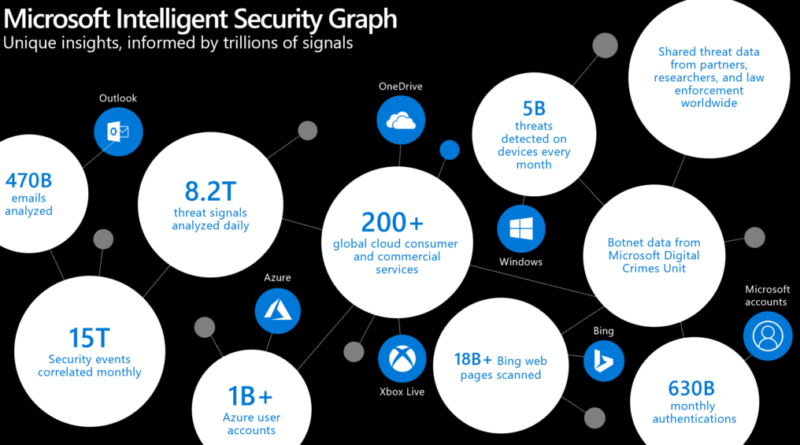
Understanding influences shaping the cybersecurity landscape, enabling digital transformation, and helping to protect our planet
The accelerated rate of digital transformation we have seen this past year presents both challenges and endless opportunities for individuals, organizations, businesses, and governments around the world. Cybersecurity is the underpinning of helping protect these opportunities. By examining the influences that are shaping the cyber landscape, and hearing from security experts, industry thought leaders, our…
The post Understanding influences shaping the cybersecurity landscape, enabling digital transformation, and helping to protect our planet appeared first on Microsoft Security. READ MORE HERE…