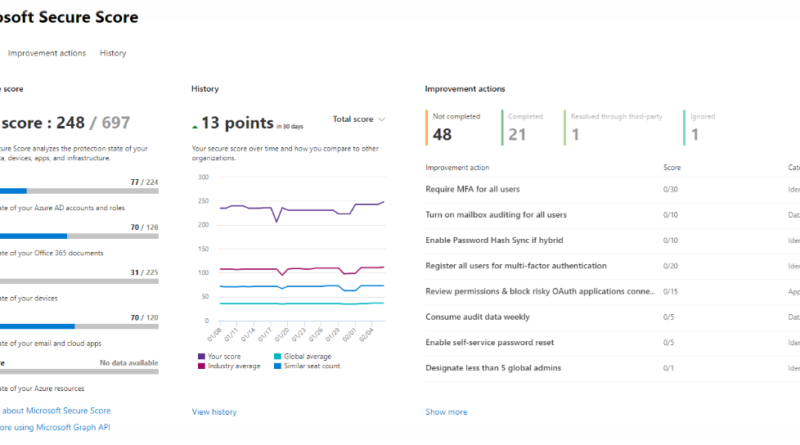
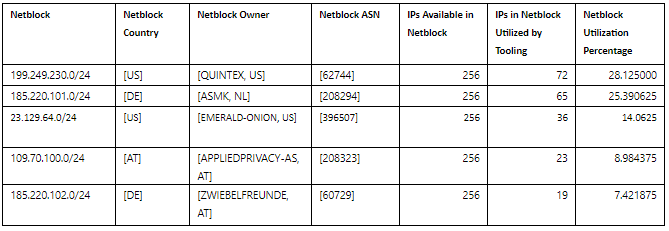
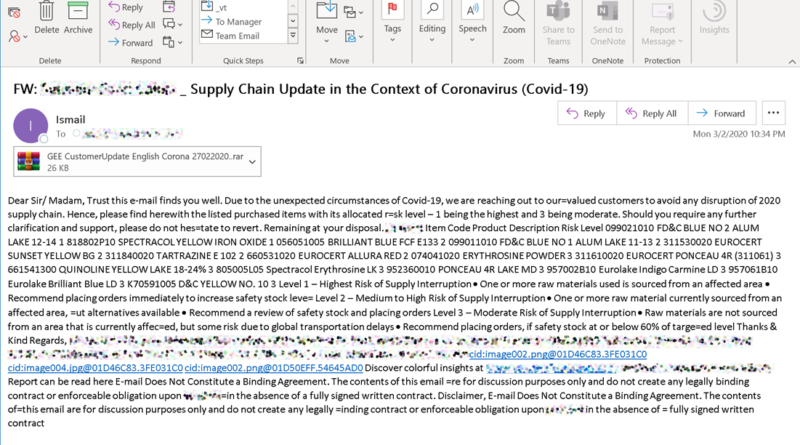
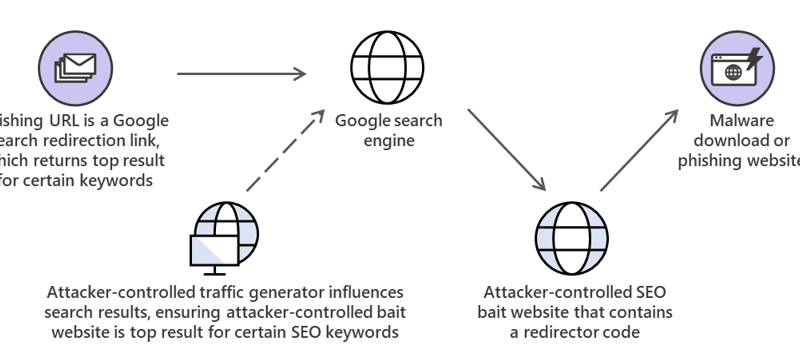
How to secure your hybrid work world with a Zero Trust approach
We are operating in the most complex cybersecurity landscape we’ve ever seen. Sophisticated and determined attackers are the norm. And we all are preparing for the next great disruption—hybrid work.
The post How to secure your hybrid work world with a Zero Trust approach appeared first on Microsoft Security. READ MORE HERE…