How to prevent phishing attacks that target your customers with DMARC and Office 365
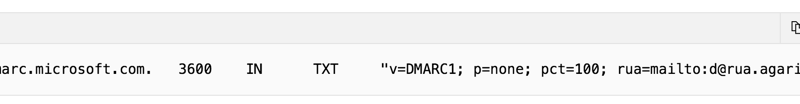
DMARC security protocol helps you take control of who can send email messages on your behalf, eliminating the ability for cybercriminals to use your domain to send their illegitimate messages.
The post How to prevent phishing attacks that target your customers with DMARC and Office 365 appeared first on Microsoft Security. READ MORE HERE…