Protect intellectual property with Govern 365 and Microsoft Purview
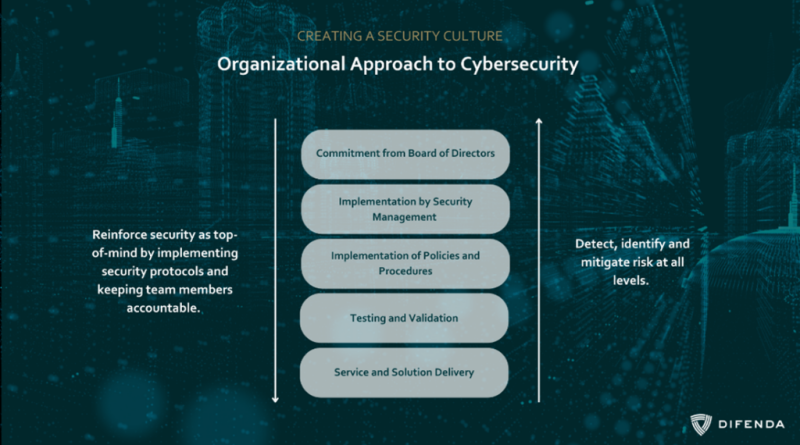
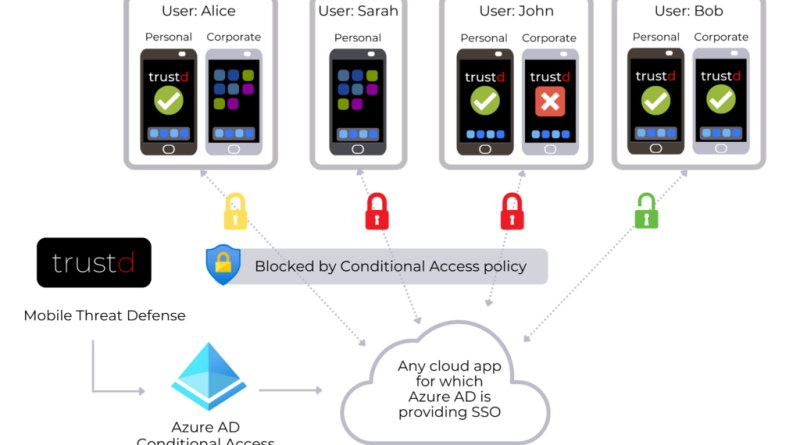
Learn how to secure sensitive information within your global supply chain with Netwoven Govern 365 and Microsoft Purview Information Protection.
The post Protect intellectual property with Govern 365 and Microsoft Purview appeared first on Microsoft Security Blog. READ MORE HERE…