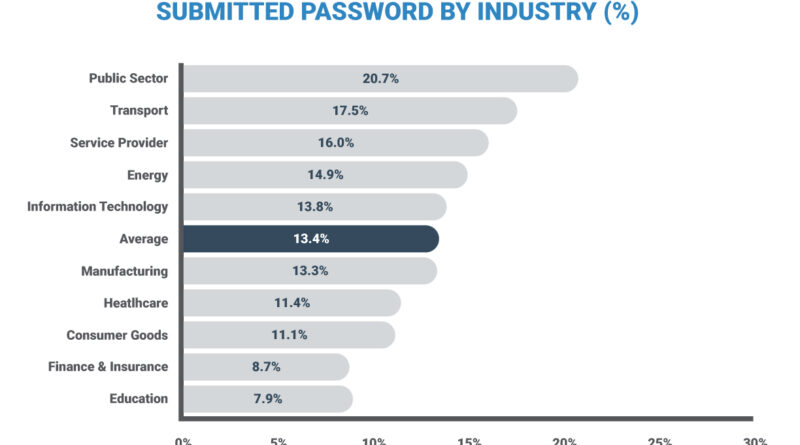
Terranova Security Gone Phishing Tournament reveals continued weak spot in cybersecurity
See which industries had the highest click rates, as well as results sorted by organization size, previous training, and more.
The post Terranova Security Gone Phishing Tournament reveals continued weak spot in cybersecurity appeared first on Microsoft Security. READ MORE HERE…