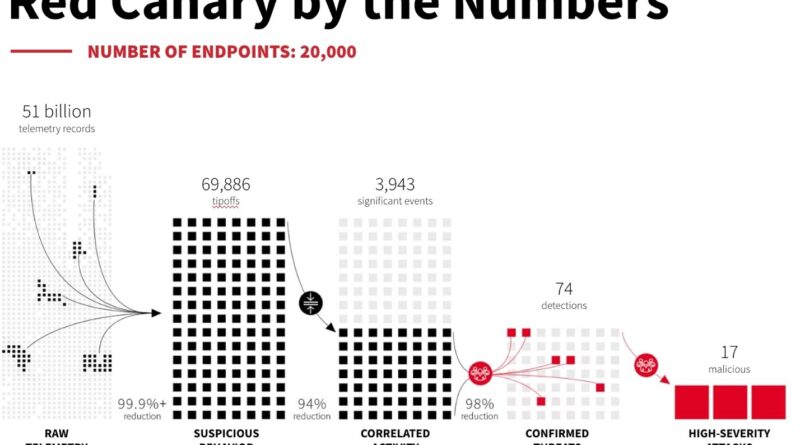
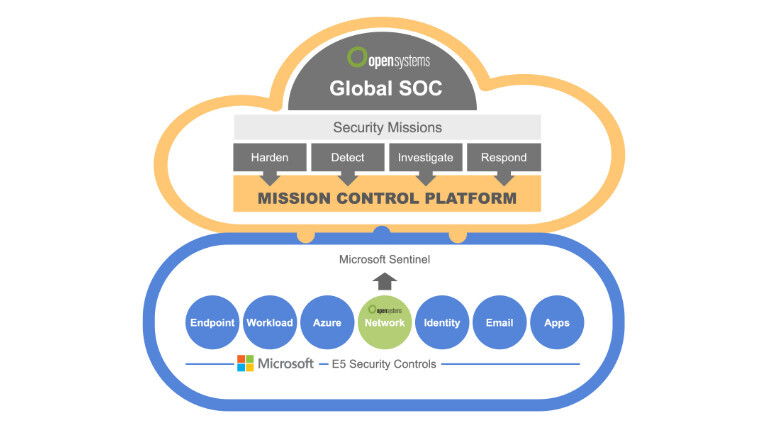
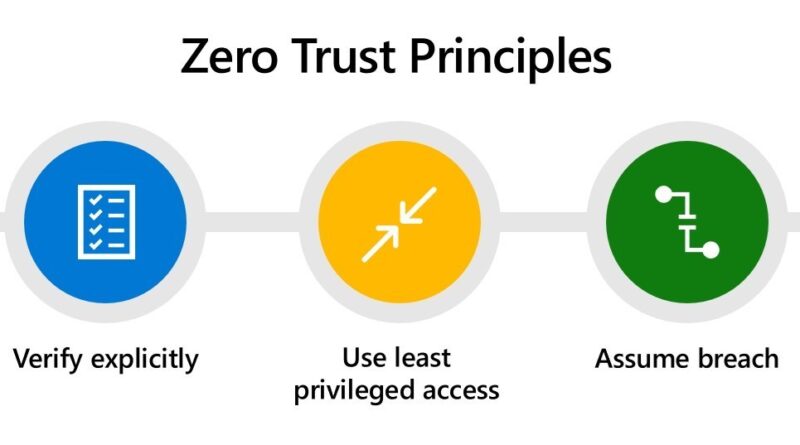
Gain real-time identity protection with Microsoft and Recorded Future
Learn how to protect your organization beyond multifactor authentication with the integration of Microsoft Sentinel with Identity Intelligence from Recorded Future.
The post Gain real-time identity protection with Microsoft and Recorded Future appeared first on Microsoft Security Blog. READ MORE HERE…