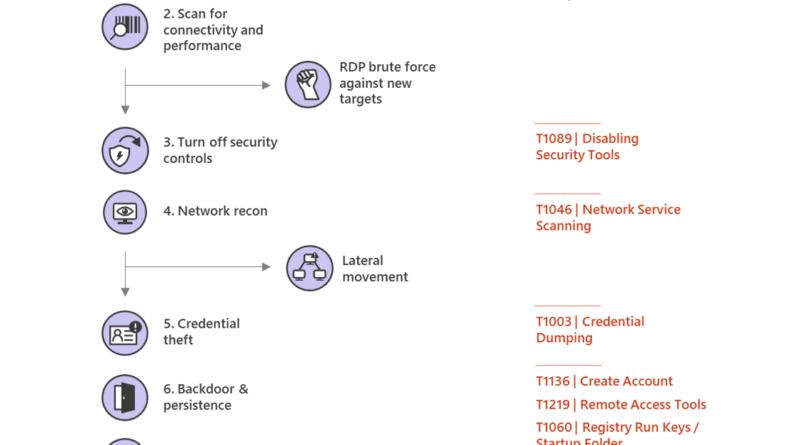
Alternative ways for security professionals and IT to achieve modern security controls in today’s unique remote work scenarios
Increased remote work has many organizations rethinking network and security strategies. In this post we share guidance on how to manage security in this changing environment.
The post Alternative ways for security professionals and IT to achieve modern security controls in today’s unique remote work scenarios appeared first on Microsoft Security. READ MORE HERE…