New security features for Windows 11 will help protect hybrid work
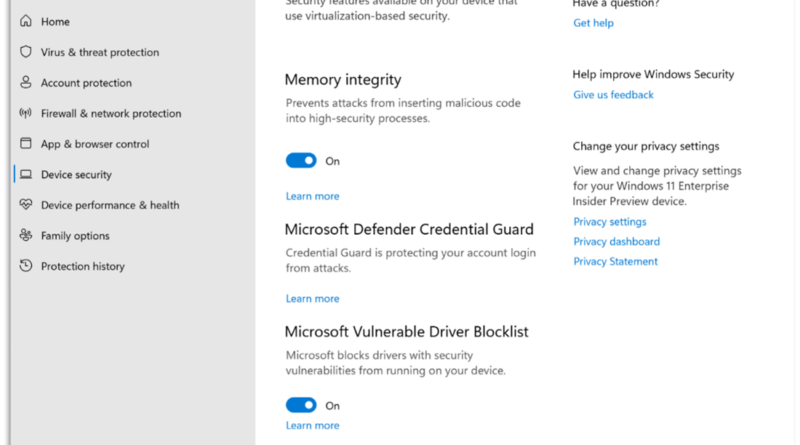
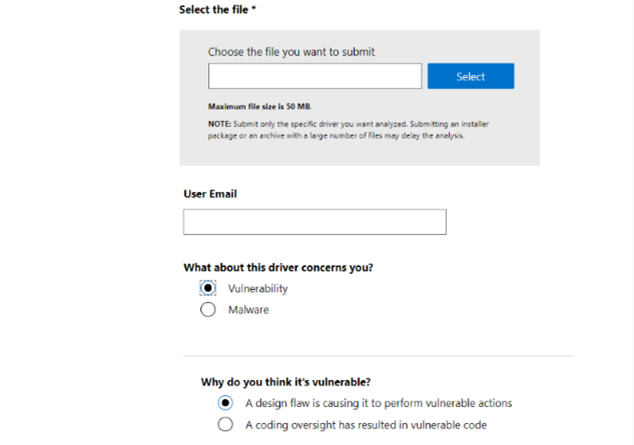
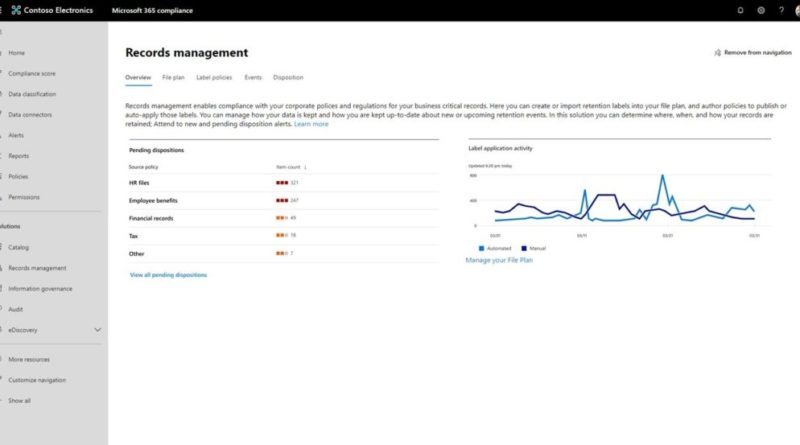
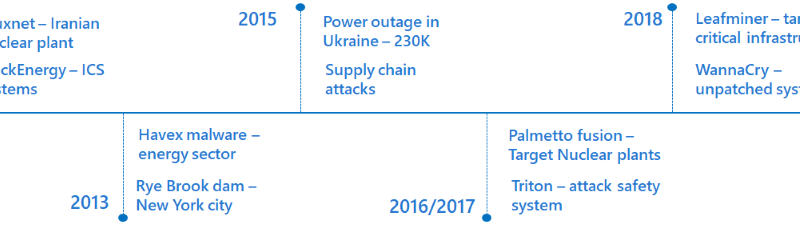
Attackers haven’t wasted any time capitalizing on the rapid move to hybrid work. Every day cyber criminals and nation states alike have improved their targeting, speed and accuracy as the world adapted to working outside the office.
The post New security features for Windows 11 will help protect hybrid work appeared first on Microsoft Security Blog. READ MORE HERE…