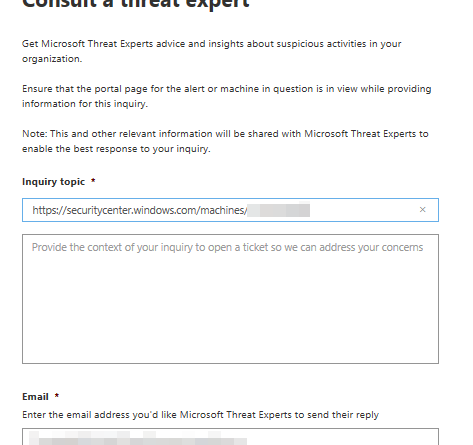
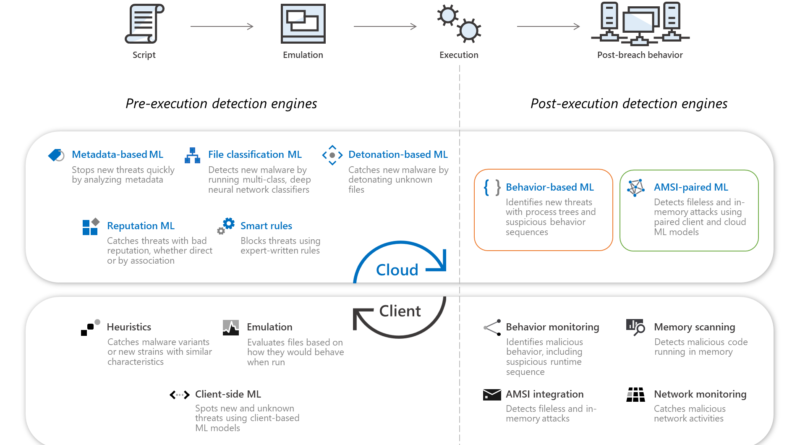
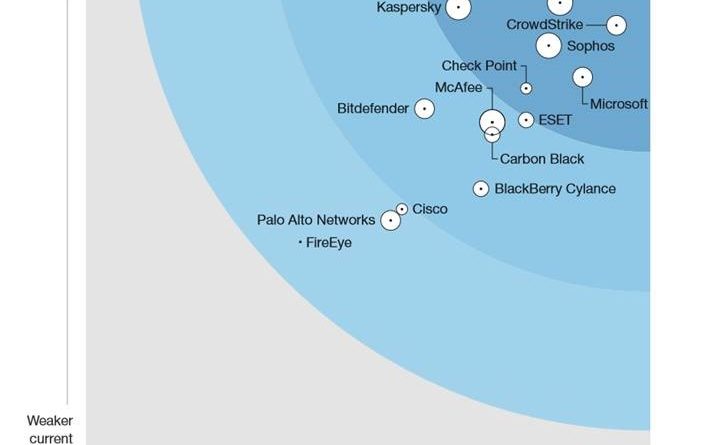
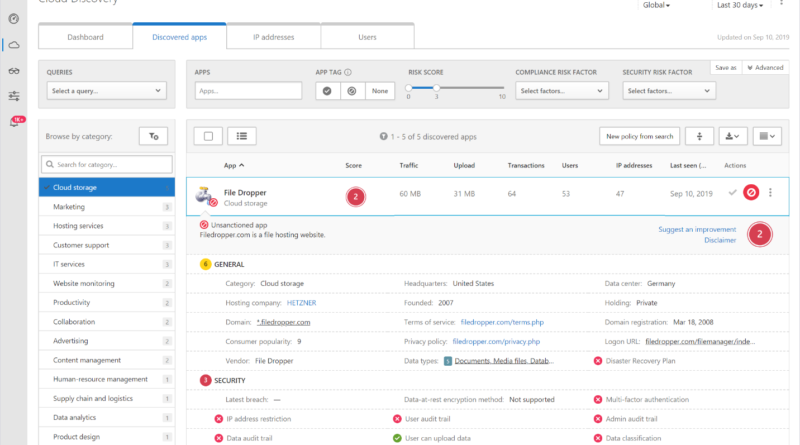
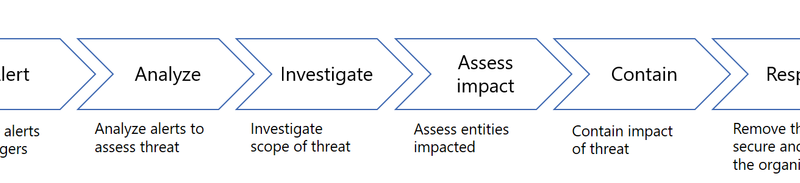
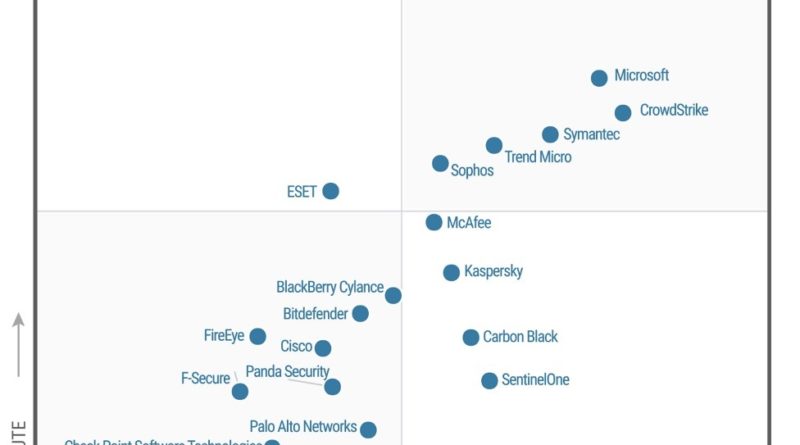
Gartner names Microsoft a Leader in the 2019 Cloud Access Security Broker (CASB) Magic Quadrant
In Gartner’s third annual Magic Quadrant for Cloud Access Security Brokers (CASB), Microsoft was named a Leader based on its completeness of vision and ability to execute in the CASB market.
The post Gartner names Microsoft a Leader in the 2019 Cloud Access Security Broker (CASB) Magic Quadrant appeared first on Microsoft Security. READ MORE HERE…