Using process creation properties to catch evasion techniques
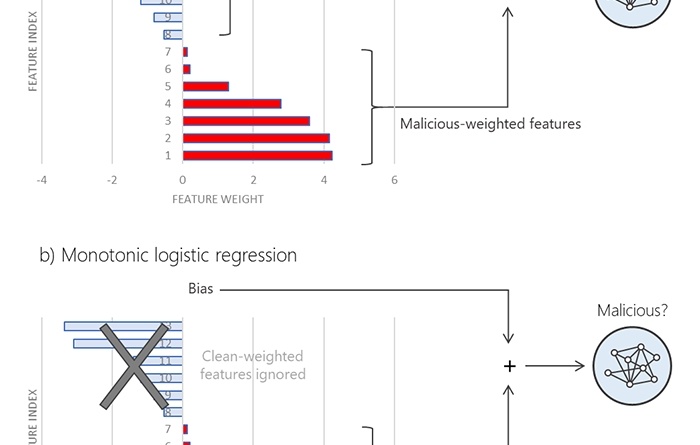
We developed a robust detection method in Microsoft Defender for Endpoint that can catch known and unknown variations of a process execution class used by attackers to evade detection. This class of stealthy execution techniques include process doppelganging, process herpadering, and process ghosting.
The post Using process creation properties to catch evasion techniques appeared first on Microsoft Security Blog. READ MORE HERE…