2022 in review: DDoS attack trends and insights
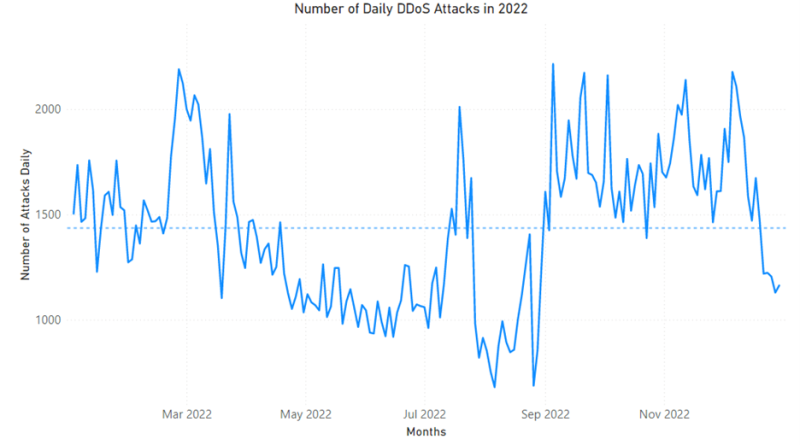
With DDoS attacks becoming more frequent, sophisticated, and inexpensive to launch, it’s important for organizations of all sizes to be proactive and stay protected. In this blog, we detail trends and insights into DDoS attacks we observed and mitigated throughout 2022.
The post 2022 in review: DDoS attack trends and insights appeared first on Microsoft Security Blog. READ MORE HERE…