Gatekeeper’s Achilles heel: Unearthing a macOS vulnerability
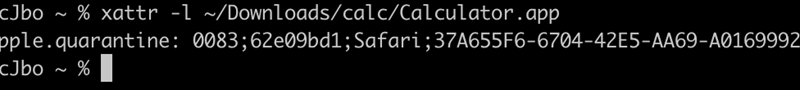
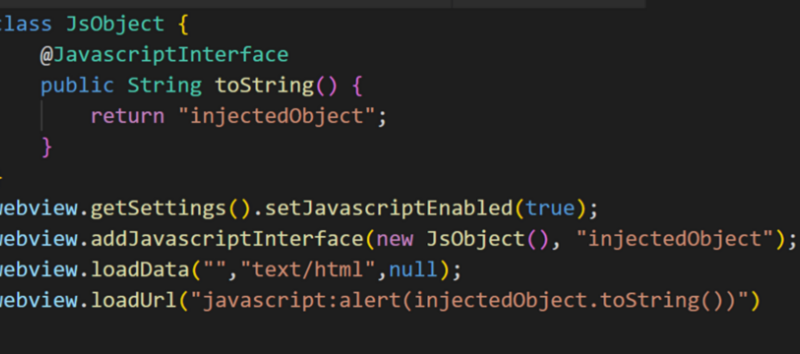
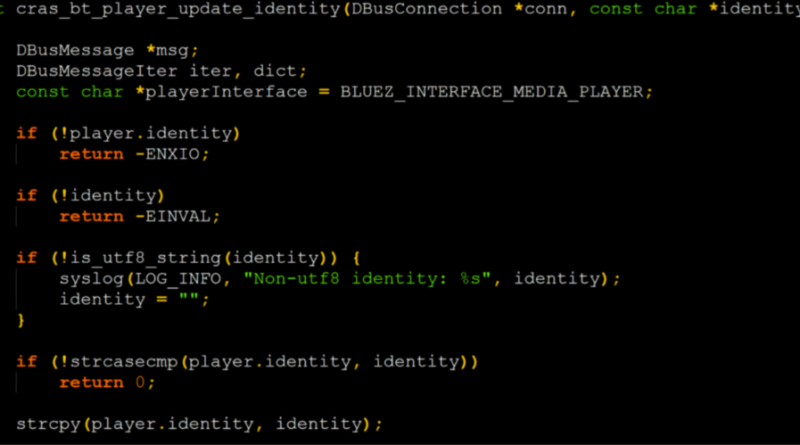
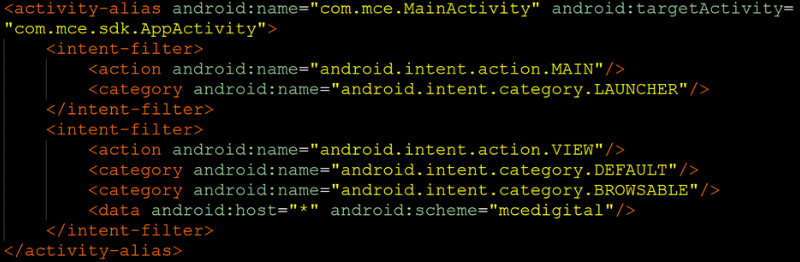
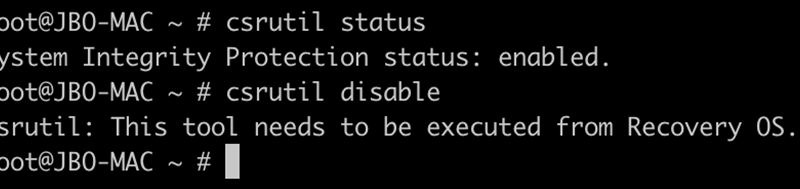
Microsoft discovered a vulnerability in macOS, referred to as “Achilles”, allowing attackers to bypass application execution restrictions enforced by the Gatekeeper security mechanism.
The post Gatekeeper’s Achilles heel: Unearthing a macOS vulnerability appeared first on Microsoft Security Blog. READ MORE HERE…