Analyzing open-source bootloaders: Finding vulnerabilities faster with AI
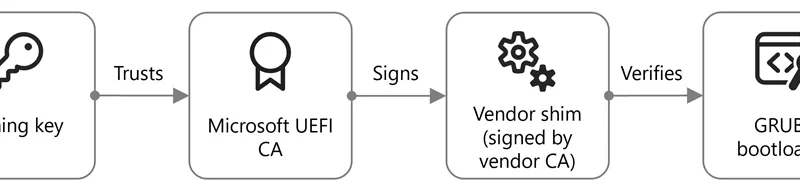
Using Microsoft Security Copilot to expedite the discovery process, Microsoft has uncovered several vulnerabilities in multiple open-source bootloaders impacting all operating systems relying on Unified Extensible Firmware Interface (UEFI) Secure Boot. Through a series of prompts, we identified and refined security issues, ultimately uncovering an exploitable integer overflow vulnerability in the GRUB2, U-boot, and Barebox bootloaders.
The post Analyzing open-source bootloaders: Finding vulnerabilities faster with AI appeared first on Microsoft Security Blog. READ MORE HERE…