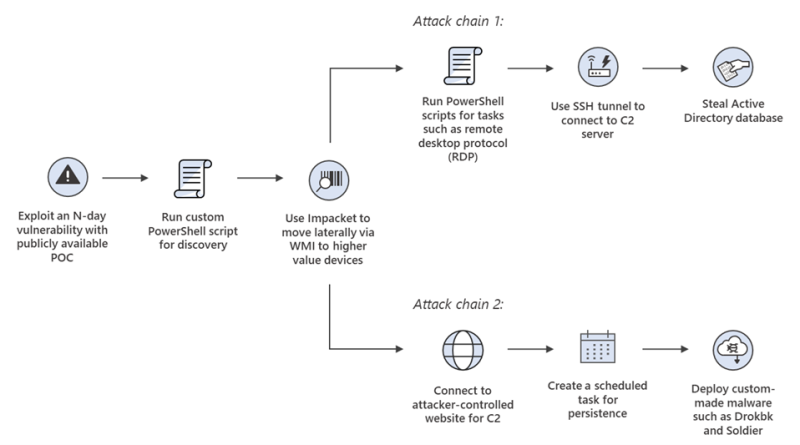
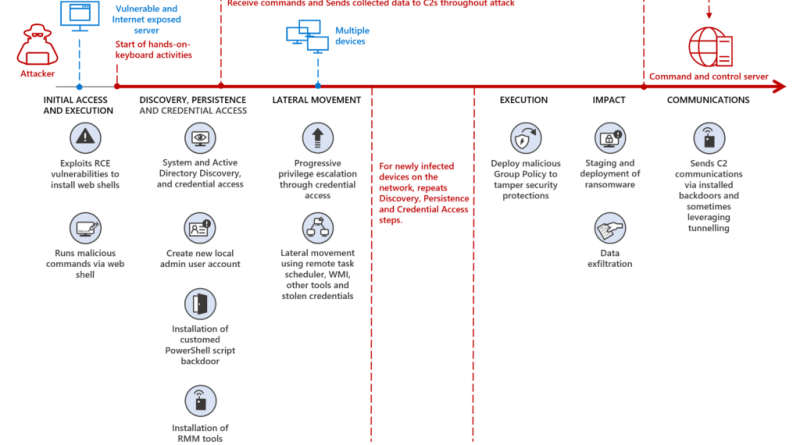
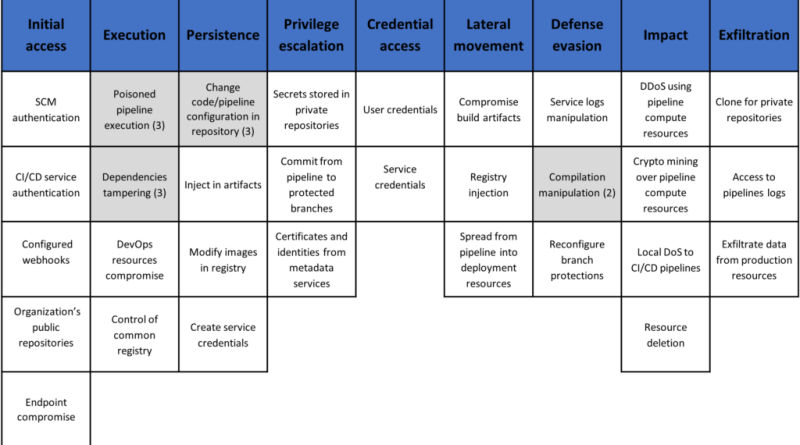
Microsoft jumps into competitive security service edge (SSE) arena
Microsoft is jumping into the competitive Secure Service Edge (SSE) arena with a software package aimed at protecting its Windows and Azure customers as well as other cloud-based enterprise resources.The new software is part of Microsoft’s Entra identity and network access suite, and it features two new elements – Entra Internet Access and Entra Private Access – that will control and secure access to cloud-based resources. Those two new pieces, coupled with Microsoft’s existing SaaS-focused cloud-access security broker (CASB), called Microsoft Defender for Cloud apps, comprise Microsoft’s SSE package.To read this article in full, please click here READ MORE HERE…