Attackers exploiting new critical OpenMetadata vulnerabilities on Kubernetes clusters
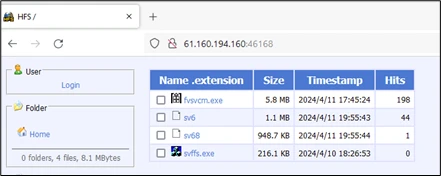
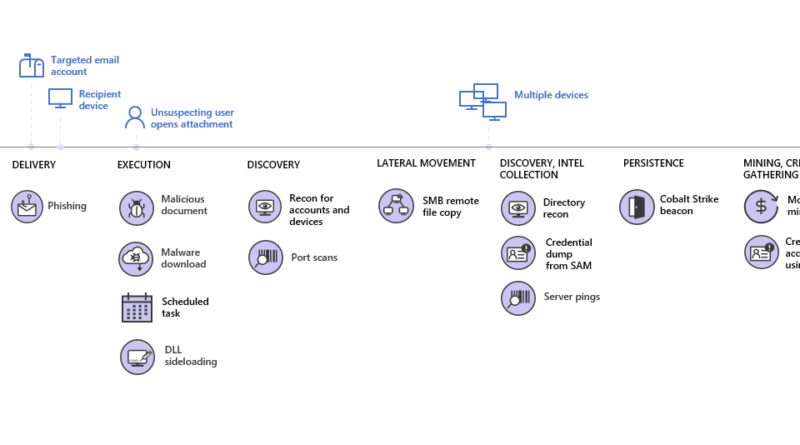
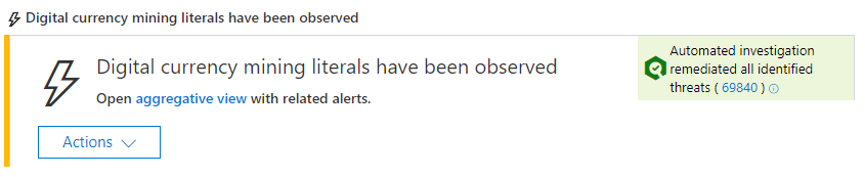
Microsoft recently uncovered an attack that exploits new critical vulnerabilities in OpenMetadata to gain access to Kubernetes workloads and leverage them for cryptomining activity.
The post Attackers exploiting new critical OpenMetadata vulnerabilities on Kubernetes clusters appeared first on Microsoft Security Blog. READ MORE HERE…