Malvertising campaign leads to info stealers hosted on GitHub
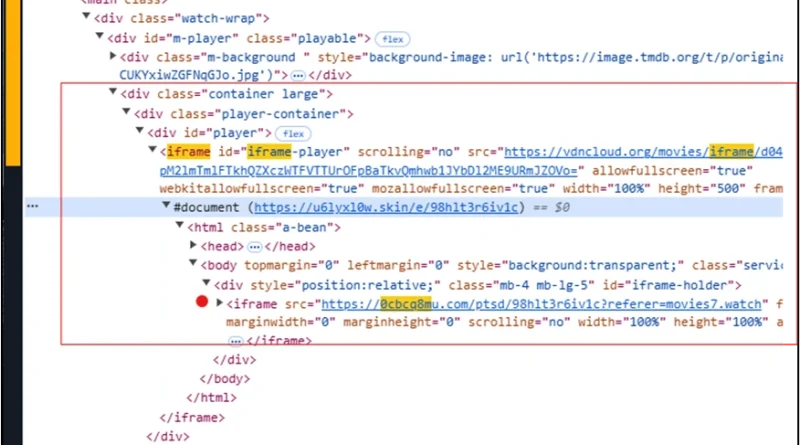
Microsoft detected a large-scale malvertising campaign in early December 2024 that impacted nearly one million devices globally. The attack originated from illegal streaming websites embedded with malvertising redirectors and ultimately redirected users to GitHub to deliver initial access payloads as the start of a modular and multi-stage attack chain.
The post Malvertising campaign leads to info stealers hosted on GitHub appeared first on Microsoft Security Blog. READ MORE HERE…