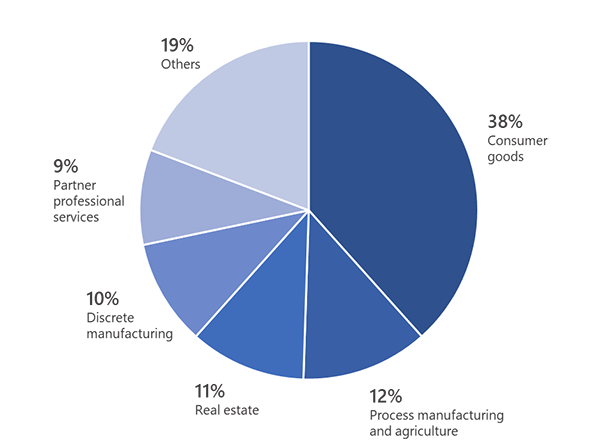
Threat actors strive to cause Tax Day headaches
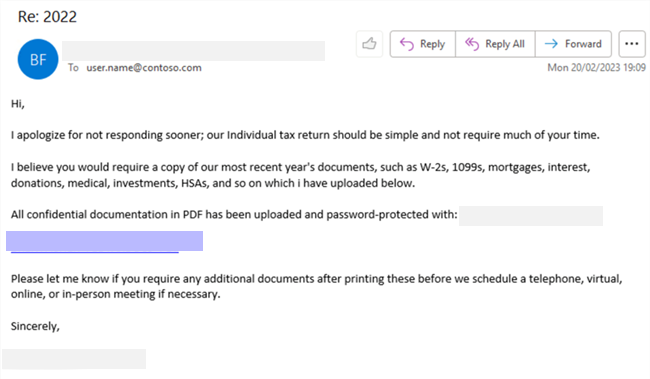
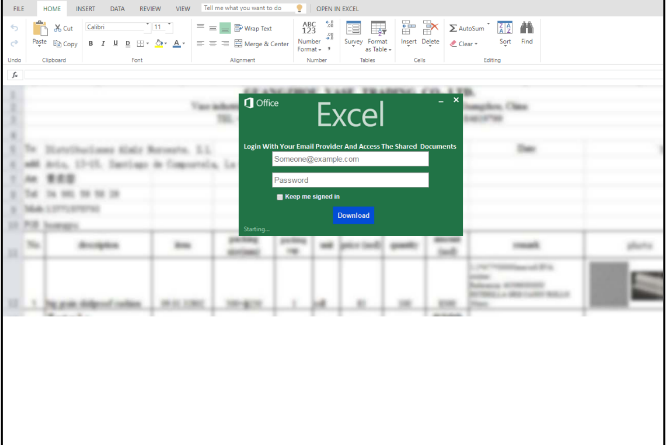
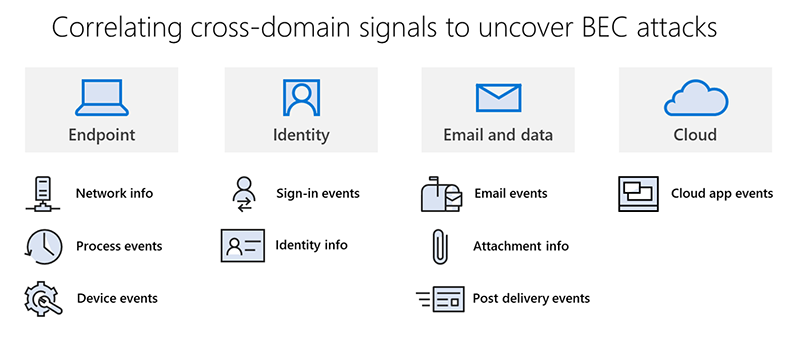
With U.S. Tax Day approaching, Microsoft has observed phishing attacks targeting accounting and tax return preparation firms to deliver the Remcos RAT and compromise target networks.
The post Threat actors strive to cause Tax Day headaches appeared first on Microsoft Security Blog. READ MORE HERE…