Phorpiex morphs: How a longstanding botnet persists and thrives in the current threat environment
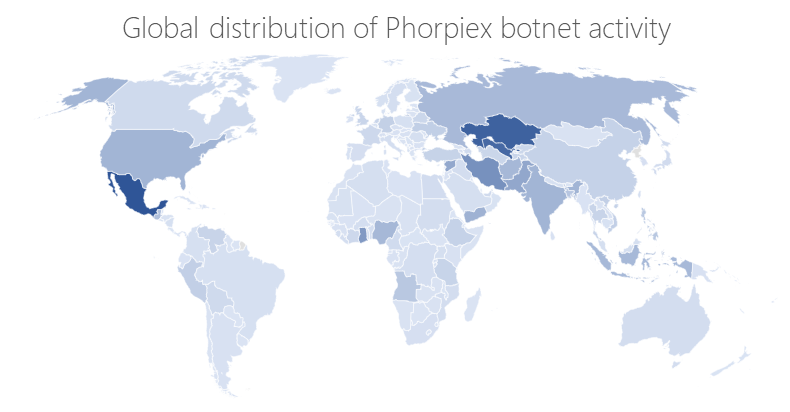
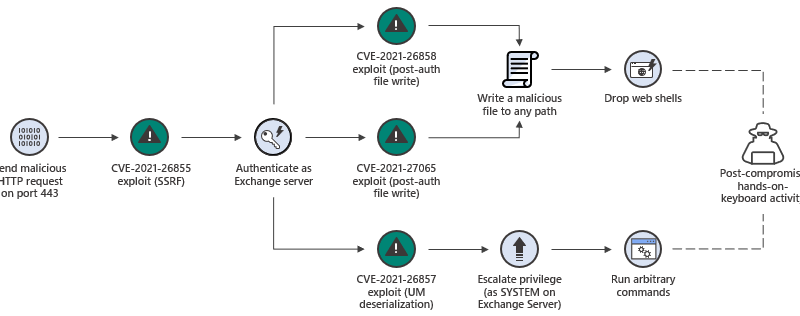
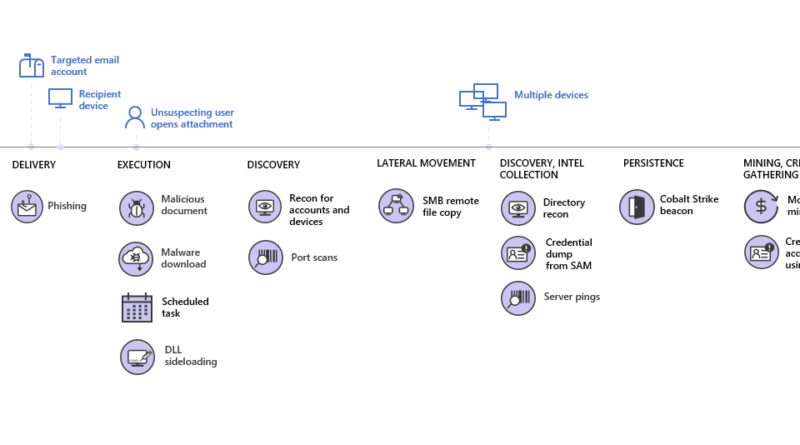
Phorpiex, an enduring botnet known for extortion campaigns and for using old-fashioned worms, began diversifying its infrastructure in recent years to become more resilient and to deliver more dangerous payloads. Today, the Phorphiex botnet continues to maintain a large network of bots and generates wide-ranging malicious activities. These activities have expanded to include cryptocurrency mining. Read our in-depth research into this botnet.
The post Phorpiex morphs: How a longstanding botnet persists and thrives in the current threat environment appeared first on Microsoft Security. READ MORE HERE…