This Week in Security News: Phishing Attacks and Ransomware
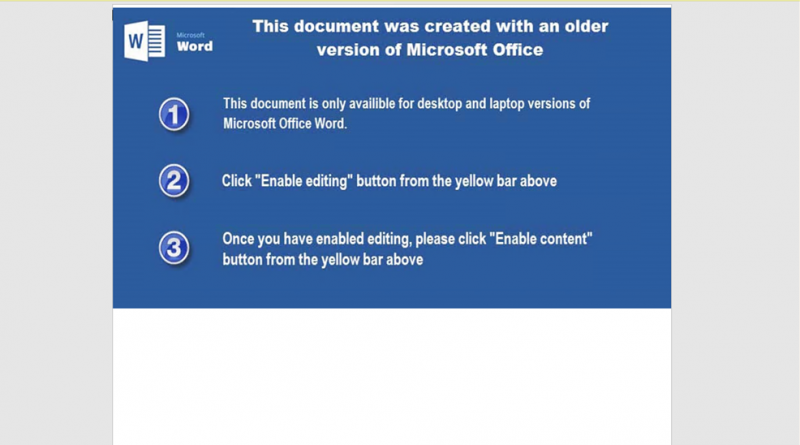
Welcome to our weekly roundup, where we share what you need to know about the cybersecurity news and events that happened over the past few days. This week, learn about schemes used in phishing and other email-based attacks. Also, learn how ransomware continues to make a significant impact in the threat landscape. Read on: New…
The post This Week in Security News: Phishing Attacks and Ransomware appeared first on . Read More HERE…