From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud
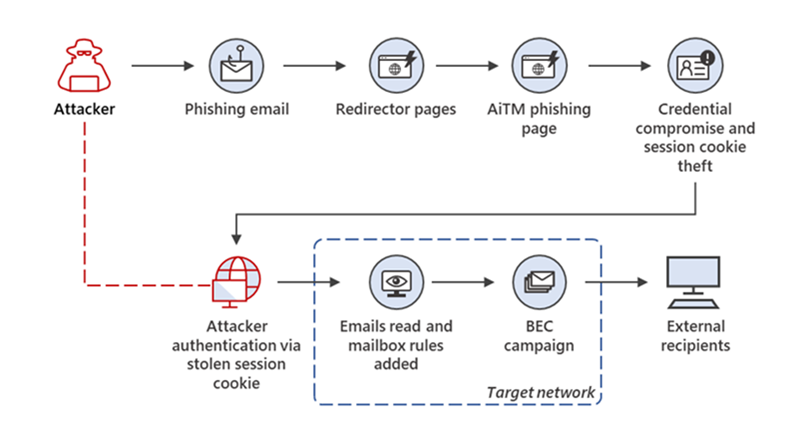
A large-scale phishing campaign that attempted to target over 10,000 organizations since September 2021 used adversary-in-the-middle (AiTM) phishing sites to steal passwords, hijack a user’s sign-in session, and skip the authentication process, even if the user had enabled multifactor authentication (MFA).
The post From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud appeared first on Microsoft Security Blog. READ MORE HERE…