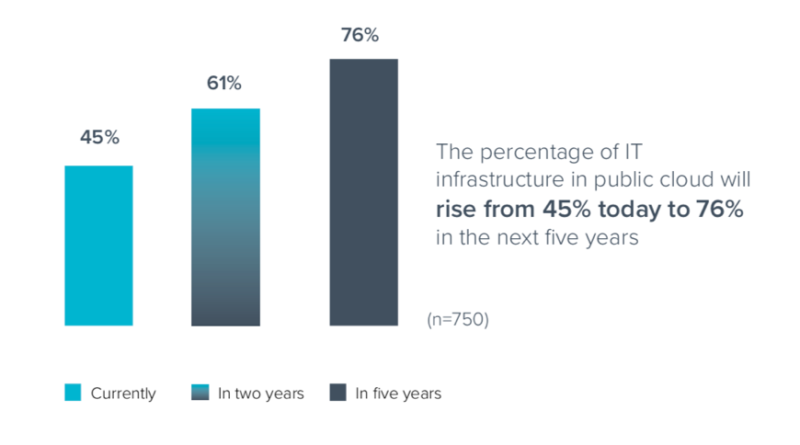
Cisco is embracing the secure-access service edge (SASE) architecture put forth by Gartner with plans to upgrade some of its existing products to reach the goal of delivering access control, security and networking to cloud services.The enterprise shift to SASE will be gradual as they figure out the best way to connect their increasingly remote workforce to distributed resources delivered from corporate data centers and as cloud services, Cisco says.Network pros react to new Cisco certification curriculum
“Flexibility will be fundamental as IT chooses among multiple security and networking capabilities that best fit their operations, regulatory requirements, and types of applications,” said Jeff Reed, senior vice president of product, Cisco’s Security Business Group in a blog post. “Security services can be predominantly delivered from the cloud to provide consistent access policies across all types of endpoints. However, globally distributed organizations may need to apply security and routing services differently according to regional requirements.” To read this article in full, please click here READ MORE HERE…
Read more