Rise in XorDdos: A deeper look at the stealthy DDoS malware targeting Linux devices
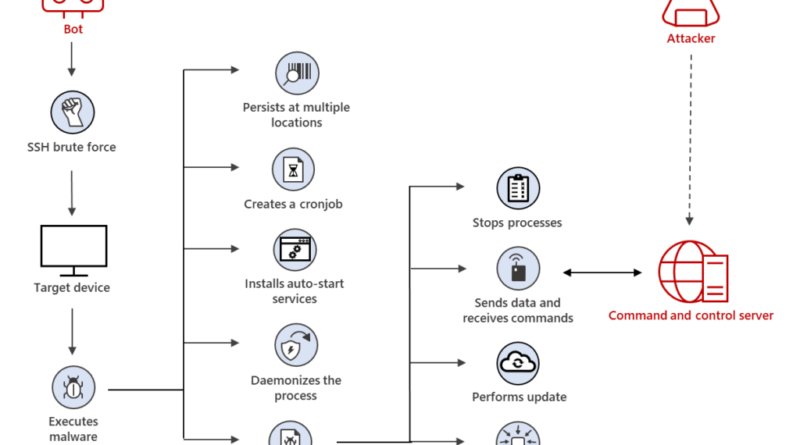
Observing a 254% increase in activity over the last six months from a versatile Linux trojan called XorDdos, the Microsoft 365 Defender research team provides in-depth analysis into this stealthy malware’s capabilities and key infection signs.
The post Rise in XorDdos: A deeper look at the stealthy DDoS malware targeting Linux devices appeared first on Microsoft Security Blog. READ MORE HERE…