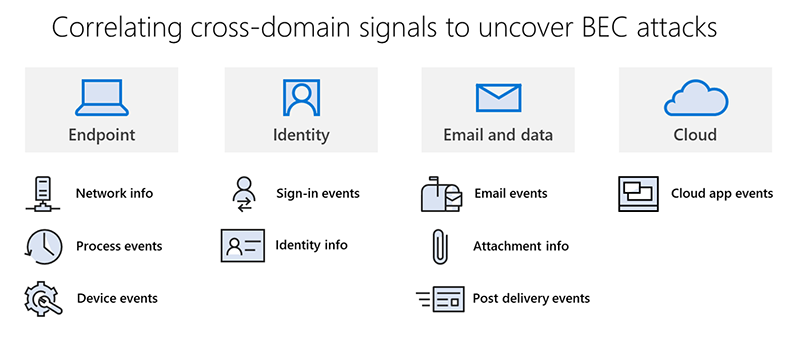
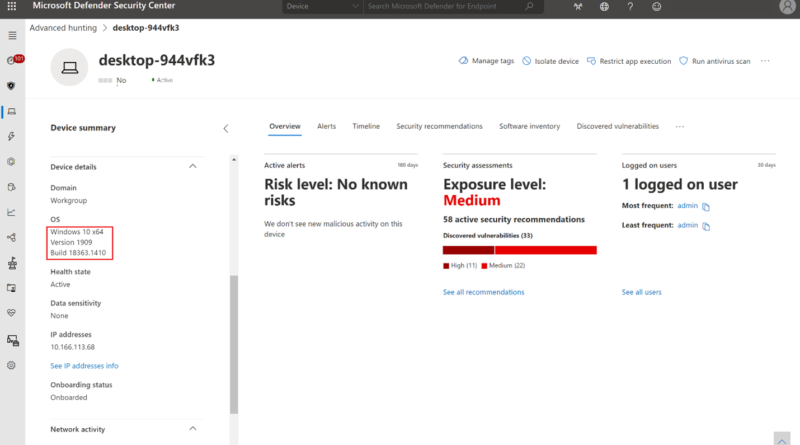
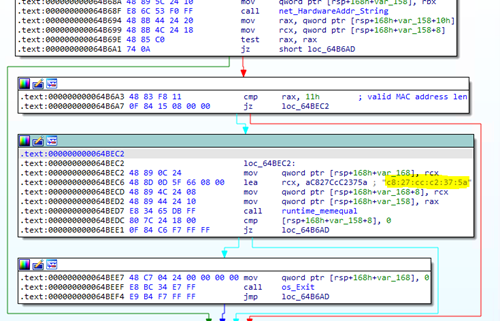
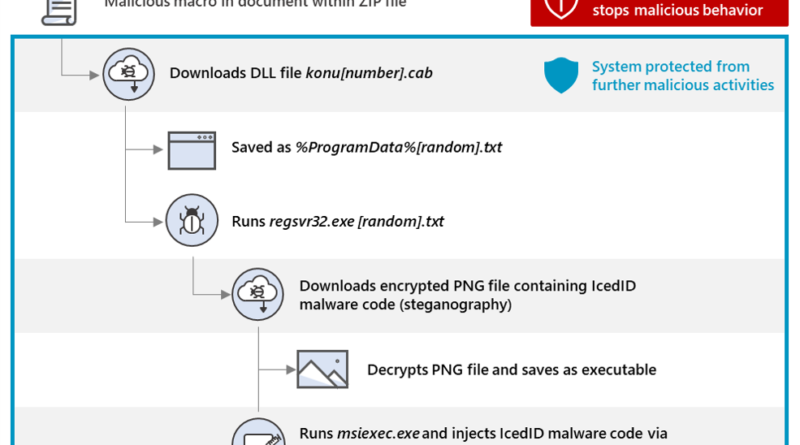
Microsoft is named a Leader in the 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms
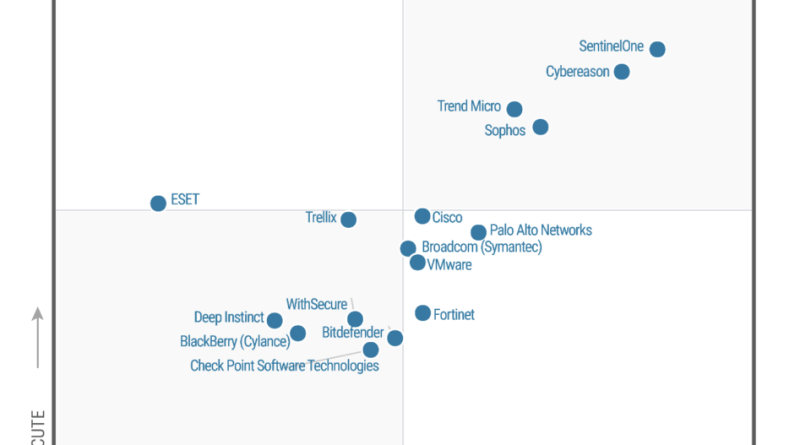
Gartner has again recognized Microsoft as a Leader in the 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms, positioned highest on the Ability to Execute.
The post Microsoft is named a Leader in the 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms appeared first on Microsoft Security Blog. READ MORE HERE…