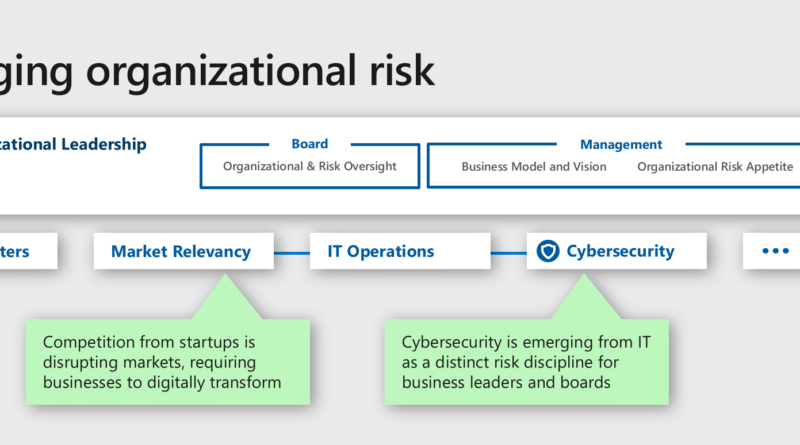
Why threat protection is critical to your Zero Trust security strategy
The corporate network perimeter has been completely redefined. Many IT leaders are adopting a Zero Trust security model where identities play a critical role in helping act as the foundation of their modern cybersecurity strategy. As a result, cybercriminals have shifted their focus and identities are increasingly under attack.
The post Why threat protection is critical to your Zero Trust security strategy appeared first on Microsoft Security. READ MORE HERE…