Afternoon Cyber Tea: Privacy, the pandemic, and protecting our cyber future

Much of our everyday life has moved online with the pandemic continuing to play a role in how we work and communicate with others. This migration has meant that security and privacy continue to remain top-of-mind for both security professionals and those who may not have given these cyber issues a second thought once before.
In this episode of Afternoon Cyber Tea, I had a chance to talk about this impact with cybersecurity expert Theresa Payton, CEO of Fortalice Solutions and co-founder of Dark Cubed.
In our discussion, we focus on Theresa’s experience with election security, social engineering, and about her book “Manipulated: Inside the Cyberwar to Hijack Elections and Distort the Truth.” We also look at how the cyber operatives behind misinformation campaigns choose their targets, and how digital empathy and human-centered design can help combat cybercrime.
“Nation-state hackers invade social issues—such as fracking, elections, or vaccinations—all while posing as Americans,” Theresa explains. She recounts how, in researching her book, she found herself speaking to a group of Macedonian hackers who targeted the 2016 election, only to discover the hackers were apolitical. “We’re pro-capitalism,” they told her, explaining how they’d created detailed models that showed how much revenue they could earn by pushing certain candidates rather than others.
“Microsoft was one of the early leaders in offering free tools to help states improve their voting technology. They looked at something that could be a revenue generator, then chose to make it about the public good instead.”—Theresa Payton, CEO of Fortalice Solutions and co-founder of Dark Cubed
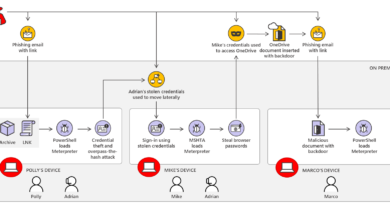
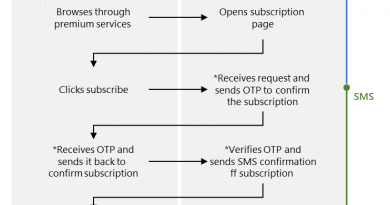
During our conversation, we talk about how social engineering attacks are often made easier by our own trusting natures, with vacation photos, birthdays, and other personal content providing the raw data hackers rely on. Since privacy settings for social media usually require users to opt-in, many users are unknowingly laying their online life out like a buffet for hackers. And, since many people don’t read the terms of service, they often have no idea what data is being collected, or what it’s being used for. Theresa mentions a study done by MIT researchers that found even anonymized data grabbed from phone records, credit card transactions, and mobile apps can be easily cross-referenced by zip code and gender to narrow the user’s identity to within just five people.
Theresa and I agree that people cannot be expected to be experts on cybersecurity or system designs, which is where digital empathy comes into play. As we get better at building security into systems, employees can be free to do what they were hired to do. “Microsoft has been leading the way in going passwordless,” Theresa says. “I’m excited that technology has finally caught up to our needs. Now we’ll only be limited by our own creative minds.”
Find out how Theresa went from working as a bank manager to handling cybersecurity at the George W. Bush White House and get some tips on how to protect yourself from social engineering schemes—listen to the full episode.
What’s next
In this ongoing podcast series, I talk with cybersecurity influencers about the evolving threat landscape and explore the promise of systems powered by AI, IoT) and other emerging tech. In every episode, we’ll look at how to empower people and organizations to create a more secure, productive digital environment.
Listen to Afternoon Cyber Tea with Ann Johnson on:
- Apple Podcasts: You can also download the episode by clicking the Episode Website link.
- Podcast One: Includes the option to subscribe—so you’re notified as soon as new episodes are available.
- CISO Spotlight page: Listen alongside our CISO Spotlight episodes, where customers and security experts discuss similar topics such as Zero Trust, compliance, going passwordless, and more.
In the meantime, bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. Or reach out to me on LinkedIn or Twitter if you have guest or topic suggestions.
READ MORE HERE