How IT leaders are securing identities with Zero Trust
The past twelve months have been a remarkable time of digital transformation as organizations, and especially digital security teams, adapt to working remotely and shifting business operations. IT leaders everywhere turned to Zero Trust approaches to alleviate the challenges of enabling and securing remote work. Using Zero Trust to secure users, data, and devices (wherever they may be) has changed from optional to a business imperative overnight.
In this short report, we surveyed IT leaders around the world to determine how they’re implementing Zero Trust practices to protect their identities and ensure their employees have secure access to resources.
- Most IT leaders are already using Zero Trust practices with their identity management solutions. While the majority of IT leaders have already implemented Zero Trust practices into their identity and access solution, only a monitory have moved on to more advanced controls that utilize automation and AI-based threat analysis.
- Multi-factor authentication (MFA) and Single Sign-On (SSO) are the most common. Additionally, a majority are analyzing risk before granting access—a critical proactive step to preventing unauthorized access to corporate resources.
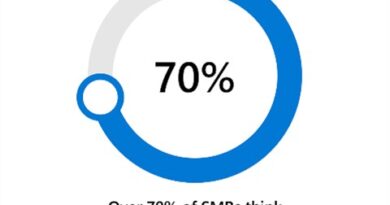
- Identities and devices are the top priority for most organizations. With employees working outside the corporate network and increasingly using personal devices, this is no surprise. However, surprisingly, the majority of IT leaders do not rate identities as the most mature component in their Zero Trust strategy.
- Zero Trust is still in infancy. Despite substantial growth in Zero Trust efforts over the past twelve months, only one in ten IT leaders report feeling very confident in their Zero Trust identity management roadmap.
Read the full report for more details.
If you’re looking for how to help prevent endpoints from being the weakest link in your security strategy, check out our Zero Trust deployment guidance for identities.
To learn more about Microsoft Security solutions visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
READ MORE HERE