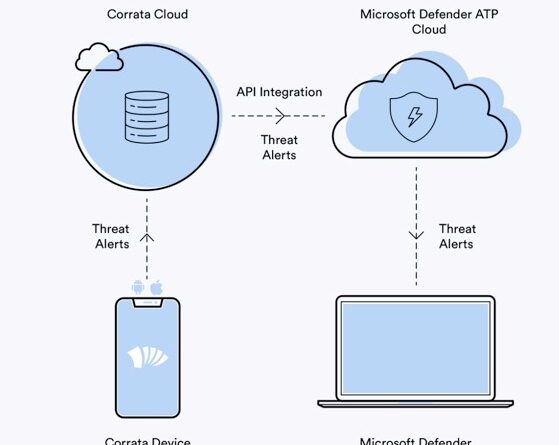
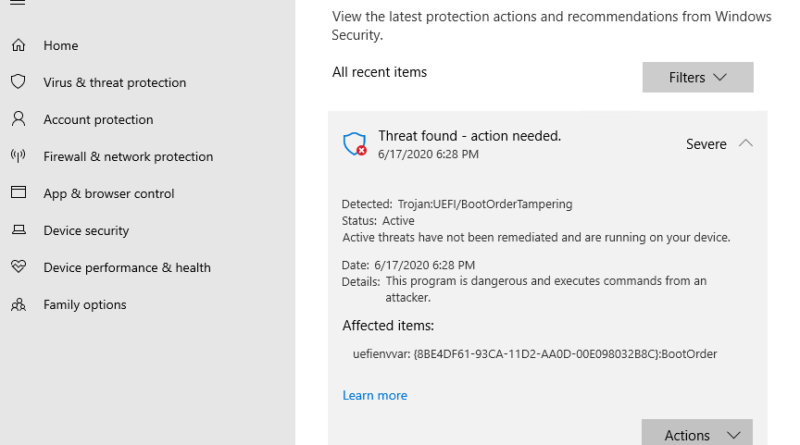
Microsoft and Corrata integrate to extend cloud app security to mobile endpoints
Corrata’s Microsoft Cloud App Security integration addresses risk mitigation through endpoint-based discovery and control for cloud apps.
The post Microsoft and Corrata integrate to extend cloud app security to mobile endpoints appeared first on Microsoft Security. READ MORE HERE…