Deep learning rises: New methods for detecting malicious PowerShell
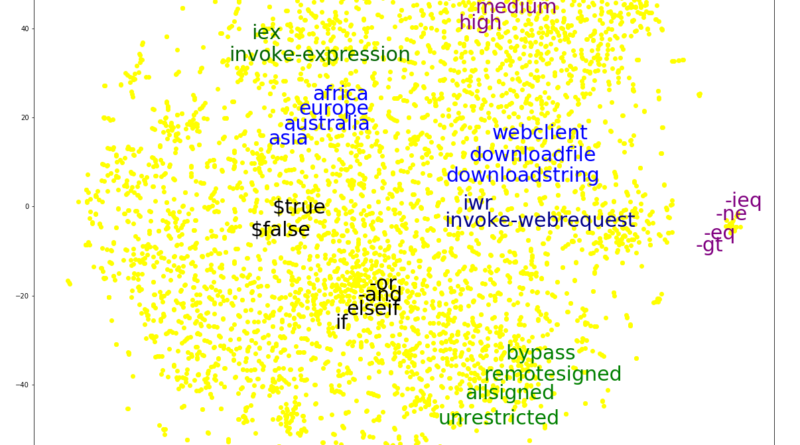
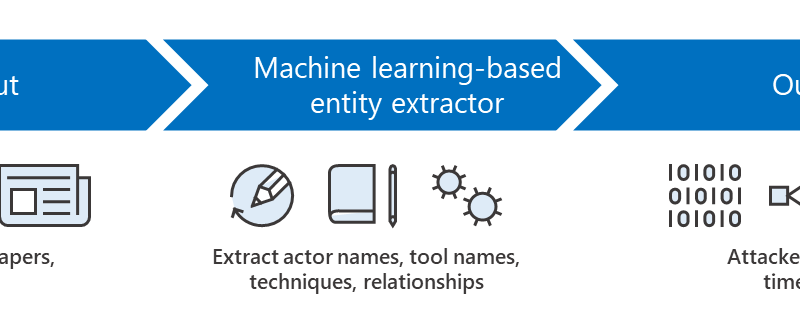
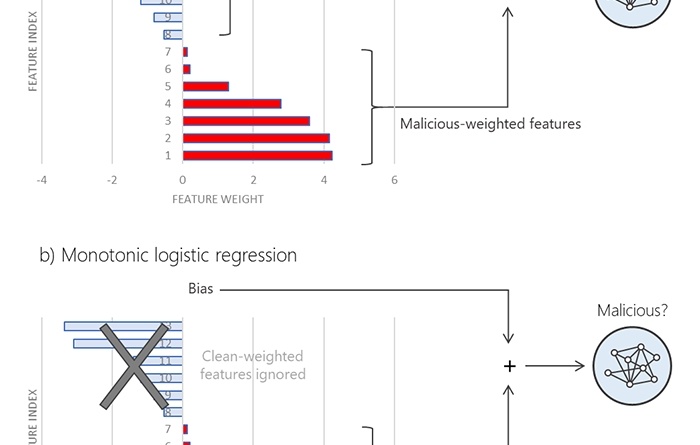
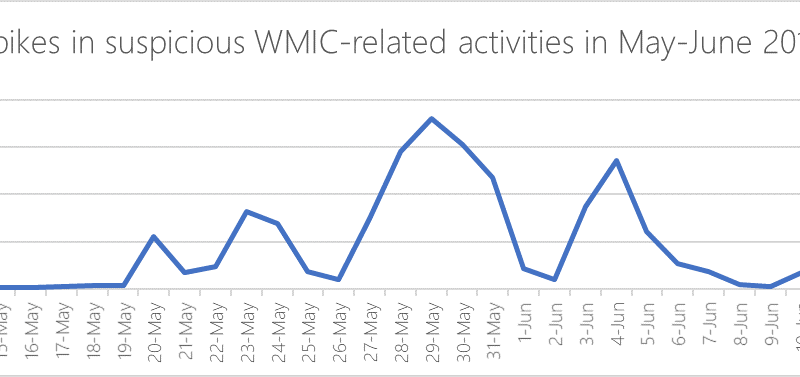
We adopted a deep learning technique that was initially developed for natural language processing and applied to expand Microsoft Defender ATP’s coverage of detecting malicious PowerShell scripts, which continue to be a critical attack vector.
The post Deep learning rises: New methods for detecting malicious PowerShell appeared first on Microsoft Security. READ MORE HERE…