Securing the Convergence of IT with OT

The Industrial Internet of Things (IIoT) is the leading edge of the convergence of Operational Technology (OT) with IT. This convergence begins with network connectivity but requires enhancements in operational procedures, technology, and training as well.
Beginning with the network, IT and OT use different protocols. Within the OT world, vendors have created many proprietary protocols over the past 50 years: MODBUS dates from 1969; ABB alone has over 20 protocols. IIoT vendors offer gateways to simplify and transform information before it moves to IT’s cloud for aggregation and processing. The volume of data can be huge, so IIoT gateways use compression, aggregation, and exception reporting to minimize network traffic. Gateways are Edge processors.
Operational procedures differ between IT and OT environments. The guiding principles of OT networks are two: safety, and service reliability. However, the IT information security principles are data availability, data integrity, and data confidentiality. These principles are orthogonal: they do not overlap. From an IT perspective, and industrial process is not “information” so falls out of scope for information security.
IT and OT processes could converge as they each evolve. DevOps breaks down the barriers between development and operations for more rapid deployment of new function without compromising controls governing software quality. Figure 1 shows a converged DevOps process:

Figure 1: Converged DevOps Process
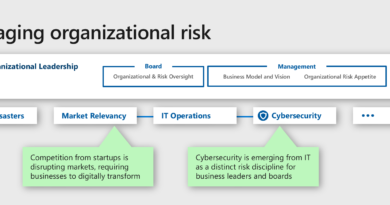
In the OT realm, enhancements to Process Hazard Analysis are driving the evolution of Cyber Process Hazard Analysis, as shown in Figure 2.

Figure 2: Cyber Process Hazard Analysis (Cyber PHA)
The OT evolution shows two processes: on the left in blue, the ongoing asset security analysis, which influences the OT Program and Governance Model in step 5 on the right. As new threats come to light, engineers update the model which flows into a new, more secure, steady state for the environment.
OT technology is evolving as core technologies offer greater processing power, storage capacity, battery life, and network connectivity. Early OT protocols had no authentication or encryption, and could not accept over-the-air software and firmware updates securely. Newer processor chips can support these requirements, but the IIoT vendors must build these capabilities, requiring larger code bases for development and some mechanism to issue patches during operations. IIoT vendors do not have experience running bug bounty programs. They will need some way to get feedback from their customers and researchers to fix problems before they get out of hand.
Training means more than ad hoc learning as the opportunity presents itself. Information security skills are scares and growing more so. Organizations need to provide additional skills to their existing staff, and may need to rely on outsourced support to bridge the gap while those new skills come on-line. But simply handing off responsibility to a third party will not eliminate risk: the organization itself will have to enhance its operational procedures to handle patch/fix requirements in time.
At Trend Micro, we understand this complexity, so we address it from different angles. Securing the connected world is one of our highest priorities. So far this year, we have launched a series of programs and partnerships to help IIoT manufacturers and their marketplaces. The Zero-Day Initiative (ZDI) includes Industrial Control Systems (ICT) defect reports. ZDI processed 202 SCADA HCI defects in the first half of 2018. Deep Security already has over 500 filters/virtual patches for OT protocols traveling over IP. Trend Micro offers guidance on deploying information security tools in the development cycle so the CD/CI process does not experience a disruption as security contexts change with production deployment. The IoT SDK helps IoT device manufacturers build core information security functions into devices during development, as with Panasonic’s In-Vehicle Infotainment (IVI) systems. By offering IoT vendors access to ZDI, Trend Micro extends its expertise in managing bug bounty programs to new entrants from outside the conventional IT realm. Partnerships with IIoT vendors such as Moxa extend 30 years of Trend’s information security expertise to a broad range of industrial control platforms. Trend Micro’s offering for telecommunications brings work-hardened network and server security to carriers for secure, reliable communications. Contact Trend Micro for more information about the threat landscape and available solutions.
For more information, please click here.
What do you think? Let me know by commenting below, or reach me @WilliamMalikTM .
Read More HERE